Microsoft Office malware: Now more users get anti-hacker, macro-blocking features

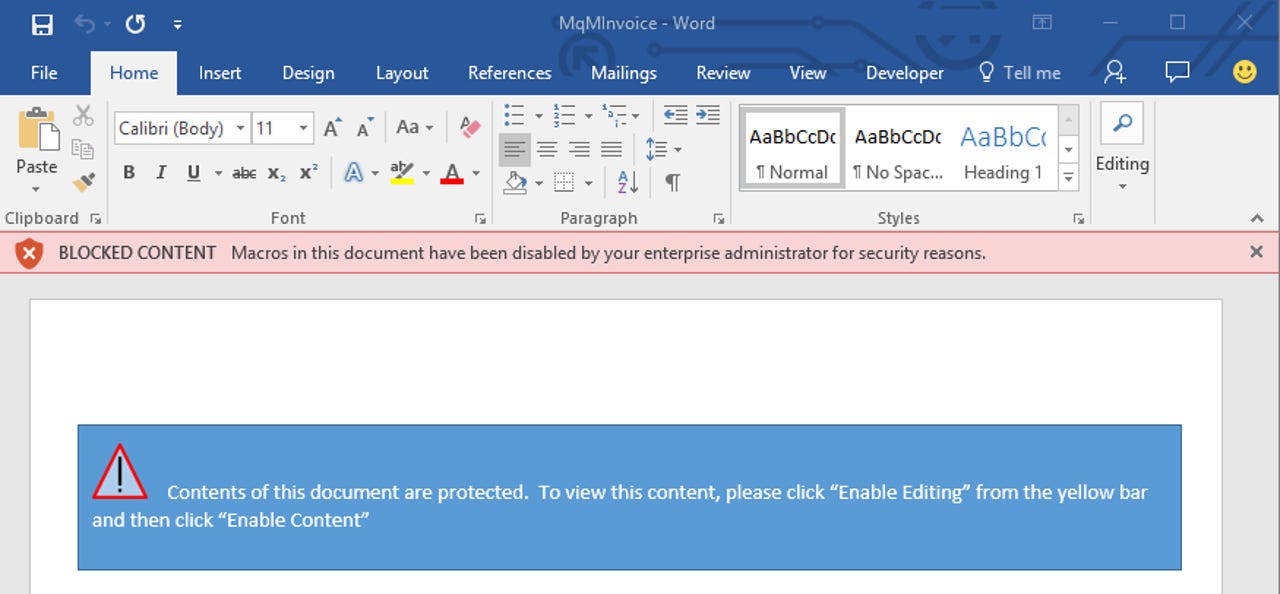
In Office 2016, if restrictions are placed on running macros, a Word document from the internet will display a red 'Blocked content' message.
Citing a growth in macro-borne threats, Microsoft has opted to give Office 2013 users a feature from Office 2016 to selectively block macros and the malware they can carry.
Office macros are a double-edged sword for the enterprise. They can improve productivity by automating routine tasks in Excel and Word, but they can be coded to deliver malware.
Even though it's been possible since the days of Office 97 to disable macros by default, users have always had the option of enabling them, which has presented attackers with a way of spreading malware since the Melissa virus in 1999. More recently, macros have been used to deliver banking Trojans and ransomware.
Fortunately, Microsoft earlier this year introduced a new feature in Group Policy for Office 2016 that allowed admins to block macros from loading in risky scenarios, such as when staff are opening Office email attachments from unknown senders, or when opening a file from Dropbox. Admins could also allow macros to run for certain trusted workflows.
Microsoft this week extended the same feature to Office 2013 because customers have been demanding it to shield networks from a growing number of macro-based malware. To enable this feature for Office 2013, admins will need to use Microsoft's Group Policy Templates for Office 2013.
Microsoft made some important changes to the way it warns users in Office 2016. In Office 2010, Word documents with macros would trigger a yellow security warning alongside an 'enable editing' button.
In Office 2016, if restrictions are placed on running macros, a Word document that arrived from the internet will not display an 'enable editing; option. Instead, users see a red message stating 'Blocked content', with an explanation that macros are disabled by the admin for security reasons.
It's likely that Office 2013 customers have been demanding Office 2016's selective macro-blocking feature due to ambiguous warnings in Office 2013.
Carnegie Mellon University CERT/CC security researcher Will Dormann recently argued that the warnings in Office 2010 and Office 2013 were "dangerous" because neither version explained the consequences of enabling macros. At the same time, it gave users the single option of enabling macros.
In Office 2016, Microsoft reverted to warnings similar to those found in Office 97, which instruct the user to enable macros if the file is from a trusted source, and to disable them if it's not. It also had three buttons: enable macros, do not open, and disable macros.
Admins implement these controls by modifying macro settings in Office 2016 applications for Visual Basic for Applications (VBA), which is commonly used to write macros.
Besides blocking VBA macros in Office documents from the internet, they can also adjust security warnings, how macros behave, and how antivirus scans encrypted VBA macros.
Meanwhile, VBA macros that are allowed to run by default need to meet certain criteria, such as being signed by a developer who uses a valid and current signature.
READ MORE ON MICROSOFT SECURITY
- Windows security: Google flags up new critical Adobe Flash Player flaw
- Microsoft: Beware this fake Windows BSOD from tech support scammers' malware
- Microsoft leads $9 million investment round in container security startup Aqua Security
- IBM, Microsoft, Oracle beware: Russia wants open source, sees you as security risk
- Microsoft Secure Boot key debacle causes security panic
- TechRepublic: Windows 10: Here's why it beats Windows 7 on security, says Microsoft
- CNET: Get to know the security features in the Edge browser