Microsoft Office vulnerabilities mean no .doc is safe
It’s an unsafe Office environment.
Two cybersecurity firms have uncovered vulnerabilities in Microsoft Office files that have allowed hackers to install malware through Word documents. The exploit -- referred to as “zero day,” because it hasn’t yet been patched -- works on all Microsoft Office versions, with attacks stretching back to late January, according to McAfee.
The suite of programs, which incorporates Word, Excel and PowerPoint, is used by 1.2 billion people, according to Microsoft.
Microsoft plans to issue an update Tuesday to address the vulnerability. Tuesday also is the day that the software giant launches its momentous Windows 10 Creators Update.
“Meanwhile, we encourage customers to practice safe computing habits online,” a Microsoft spokesperson said in a statement, “including exercising caution before opening unknown files and not downloading content from untrusted sources to avoid this type of issue.”
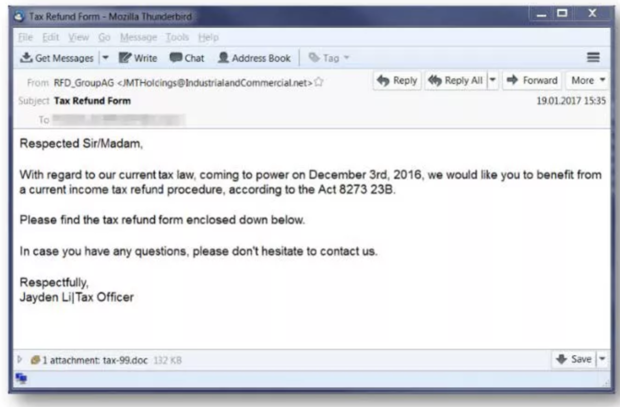
The malware can be disguised as important files or documents sent over email, meaning a student’s homework or an office presentation could be harboring the next attack. You might even have to worry about your finances: Researchers have found that during tax season hackers send spam emails pretending to be from a “tax officer” with a fake tax refund form attached as a Word document, with malware embedded.
The attack cannot be activated if people open the documents in Office’s protected view, McAfee said.
The exploit works like this: The attacker gives an RTF file a .doc extension name. Once the victim opens the disguised text document, it connects to the attacker’s servers and automatically downloads an HTML application file and launches it, giving the hacker full control of your device.
If the exploit is successful, it closes the downloaded Word document and creates a fake copy of it, while quietly installing malware in the background.
The vulnerability comes from Windows Object Linking and Embedding feature, according to FireEye. The cybersecurity firm said it’s informed Microsoft and is coordinating with the company to address the vulnerability.
CNET Magazine: Check out a sampling of the stories you’ll find in CNET’s newsstand edition.
Tech Enabled: CNET chronicles tech’s role in providing new kinds of accessibility.
This article was originally published on CNET.com.