
Contrary to what Ars and the rest of the world reported Friday, none of the published exploits stolen from the National Security Agency work against currently supported Microsoft products. This is according to a Microsoft blog post published late Friday night.
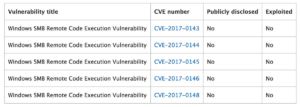
That's because the critical vulnerabilities for four exploits previously believed to be zero-days were patched in March, exactly one month before a group called Shadow Brokers published Friday's latest installment of weapons-grade attacks. Those updates—which Microsoft indexes as MS17-010, CVE-2017-0146, and CVE-2017-0147—make no mention of the person or group who reported the vulnerabilities to Microsoft. The lack of credit isn't unprecedented, but it's uncommon, and it's generating speculation that the reporters were tied to the NSA. In a vaguely worded statement issued Friday, Microsoft seemed to say it had had no contact with NSA officials concerning any of the exploits contained in Friday's leak.Microsoft provided the following table showing when various vulnerabilities were patched:
| Code Name | Solution |
| “EternalBlue” | Addressed by MS17-010 |
| “EmeraldThread” | Addressed by MS10-061 |
| “EternalChampion” | Addressed by CVE-2017-0146 & CVE-2017-0147 |
| “ErraticGopher” | Addressed prior to the release of Windows Vista |
| “EsikmoRoll” | Addressed by MS14-068 |
| “EternalRomance” | Addressed by MS17-010 |
| “EducatedScholar” | Addressed by MS09-050 |
| “EternalSynergy” | Addressed by MS17-010 |
| “EclipsedWing” | Addressed by MS08-067 |
A measure of relief
The revelation that none of the highly advanced exploits work against supported Microsoft products brings a measure of relief to some of the more dire warnings sounded 24 hours earlier. It means that most home and small-office users are likely to be safe, since their systems are likely to have automatically installed the critical updates weeks ago. Computers in larger organizations, however, can often remain two or more months behind Microsoft's patch schedule, as administrators test the updates to ensure they're compatible with intranets and other internal systems. That means that some of the most sensitive and mission-critical networks may still be vulnerable to the four exploits, which are known as EternalBlue, EternalChampion, EternalSynergy, and EternalRomance.
Security researchers have taken to social media sites to speculate on the circumstances that led to Microsoft killing all four of would-be zero-days one month before they were published on the Internet. As mentioned above, one theory is that someone from the NSA privately gave Microsoft warning that the leaks were imminent. As reported Friday by Emptywheel, a Shadow Brokers release from early January gave NSA officials notice of some of the exploit names obtained by the mysterious person or group and later included in Friday's release. The extra time Microsoft needed to patch the bugs might possibly have something to do with February's unprecedented canceling of Patch Tuesday.A second possibility is that Microsoft paid Shadow Brokers for the vulnerabilities and didn't make that purchase public. In any event, and as noted by security commentator Ryan Naraine on Twitter, Microsoft's March Patch Tuesday bulletins explicitly said none of the Shadow affected vulnerabilities were being actively exploited, a claim company officials surely knew was false had the flaws been disclosed either by the NSA or the leakers.
Another plausible possibility is that Microsoft patched the vulnerabilities by chance and without advanced warning of the NSA. When the Shadow Brokers recognized that the exploits were no longer valuable zero-days, they published them in a campaign designed to sow confusion. That theory is consistent with Friday's release of other exploits that remained unpatched in unsupported Microsoft products including Windows XP, Windows Server 2003, Exchange 2007, and IIS 6.0. Under this theory, none of the exploits published Friday worked on supported Microsoft products, so the Shadow Brokers decided to use them in a propaganda campaign. The problem with this theory, however, is the coincidental timing of the patch and leak seem highly unlikely.
Aside from the mystery surrounding the patching of these vulnerabilities one month ahead of the exploits, the other major question is how multiple security researchers and news outlets all incorrectly reported the exploits targeted fully updated products that remained supported by Microsoft. The answer is that researchers didn't test the exploits against fully updated versions of Windows 7 and other Supported Microsoft products.
The zero-day assessment "was based on best information at the time and early testing, which turned out to be incorrect," the security commentator and researcher who goes by the moniker SwiftOnSecurity wrote on Twitter. "Because there was no indication Microsoft patched these bugs, researcher systems did not include last month's patches, so they [the exploits] still worked."
Other researchers, including Kevin Beaumont and Matthew Hickey, said they made the same critical mistake. Ars and dozens of other publications then reported those mistaken findings. Ars regrets the error.
reader comments
102