
Extending its commitment to data security and user privacy, Microsoft has just announced the addition to its platform of something it calls Azure confidential computing.
In a post on the official Azure Blog, the service's Chief Technology Officer, Mark Russinovich, has revealed that through this announcement, Microsoft's platform is the first to bring encryption of data in use to the public cloud, something which was missing previously.
For those not familiar, there are three states of data in the cloud and in general: data in transit, at rest, and in use. Data in transit refers to data that is being actively moved from one location to another, through the network - both public and private. Data at rest is inactive data that is not being used and is stored in any form, either on physical media, in databases, data warehouses or anything else of the sort. Finally, data in use refers to data stored in RAM or CPU cache, and in the context of cloud computing and SaaS (Software-as-a-Service), data which is being presently processed by cloud applications.
The culmination of an over four year effort between the Azure, Windows, Microsoft Research, and Developer Tools teams in Redmond, as well as Intel, the software and hardware tool set referred to as Azure confidential computing seeks to alleviate the concerns of those who've yet to move their data to the cloud, for fear of breaches. As the blog entry points out:
With confidential computing, they can move the data to Azure knowing that it is safe not only at rest, but also in use from the following threats:
- Malicious insiders with administrative privilege or direct access to hardware on which it is being processed
- Hackers and malware that exploit bugs in the operating system, application, or hypervisor
- Third parties accessing it without their consent
Confidential computing ensures that when data is “in the clear,” which is required for efficient processing, the data is protected inside a Trusted Execution Environment (TEE - also known as an enclave), an example of which is shown in the figure below. TEEs ensure there is no way to view data or the operations inside from the outside, even with a debugger. They even ensure that only authorized code is permitted to access data. If the code is altered or tampered, the operations are denied and the environment disabled. The TEE enforces these protections throughout the execution of code within it.
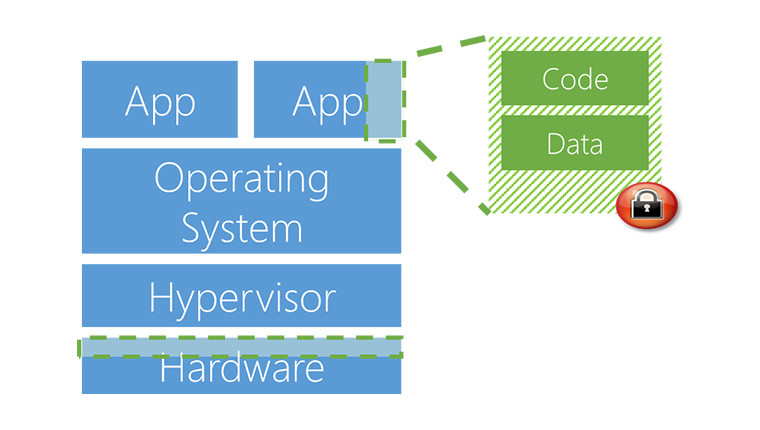
Regarding Trusted Execution Environments (TEEs), these are created on the platform in such a way as to allow developers to use their existing code, without the need to make any changes. At present, Azure confidential computing supports two TEEs, one software-based, and the other hardware-based.
The first one is Virtual Secure Mode or VSM, a software-based solution implemented by Hyper-V in both Windows 10 and Windows Server 2016. In this instance, Hyper-V prevents the running of administrator code on either the computer or server, as well as the viewing of content and modification of its execution within the VSM enclave.
For those who do not wish to have anything to do with either Microsoft or its Azure platform, a second implementation, Intel SGX, is offered on the hardware side. It is worth noting that Microsoft is the first to offer SGX-capable servers at present, but Russinovich is quick to point out that the firm is "working with Intel and other hardware and software partners to develop additional TEEs" and will support them as soon as they become available.
This is however not the first time Microsoft has used TEEs/enclaves. The Redmond giant has also implemented them in its Coco Framework, geared towards enterprise blockchain use. To coincide with the announcement of Azure confidential computing, Microsoft is also announcing the extension of its Always Encrypted functionality by implementing the underlying technology in the Coco Framework in Azure SQL Database and SQL Server, thus providing the encryption of data in use.
Azure confidential computing is only the latest in a series of initiatives on Microsoft's part to further emphasize the company's privacy and security focus. Among other things, Azure Information Protection ensures that data is protected in the cloud, an initiative which was recognized via Azure's HITRUST security certification back in January.
Those who wish to try out the tool set described above can sign up now for early access, or wait until September 25 for Microsoft's Ignite event, where Russinovich will demonstrate the use of enclaves in Azure.
















3 Comments - Add comment