With the release of Windows 10 Fall Creators Update last week, the "Controlled Folder Access" that Microsoft touted in June is now live for millions of users.
As the name hints, the Controlled Folder Access feature allows users to control who can access certain folders.
The feature works on a "block everything by default" philosophy, which means that on a theoretical level, it would be able to prevent ransomware when it tries to access and encrypt files stored in those folders.
The benefits of using Controlled Folder Access for your home and work computers are tangible for anyone that's fearful of losing crucial files to a ransomware infection.
If you want to give Controlled Folder Access a go, below are the basic steps to enable it on your PC.
Step 1
Press the Start button and type "Windows Defender Security Center." Select the option when visible. The following window should appear.
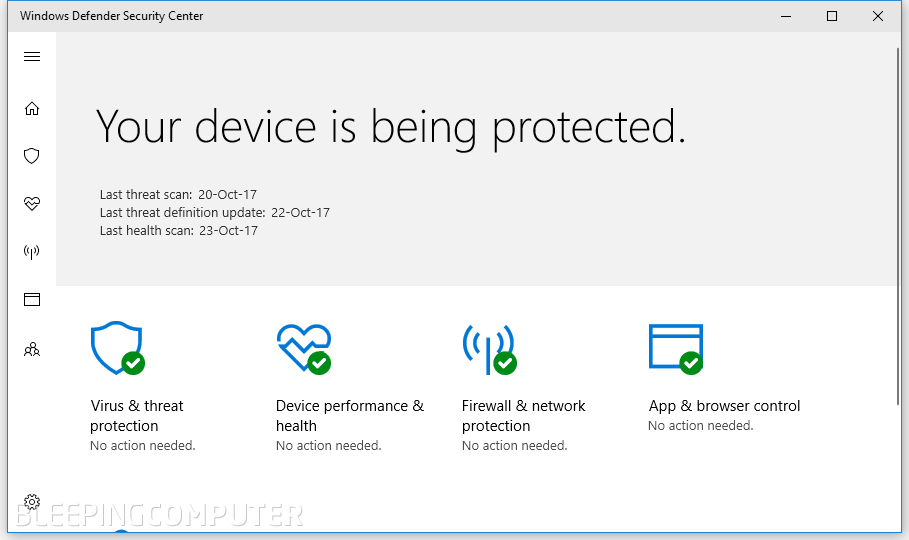
There's a high chance you might select the wrong option and end up in the Windows Defender Settings section. In this case, just press the obvious "Open Windows Defender Security Center" button that appears at the top of the window.
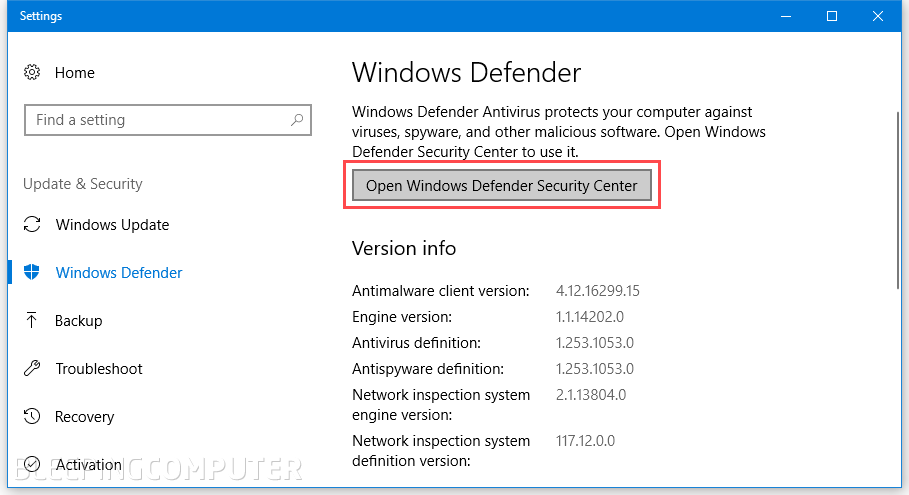
Step 2
In the "Windows Defender Security Center" select the second option in the side menu named "Virus & threat protection" and then select the "Virus & threat protection settings" option from the main window.
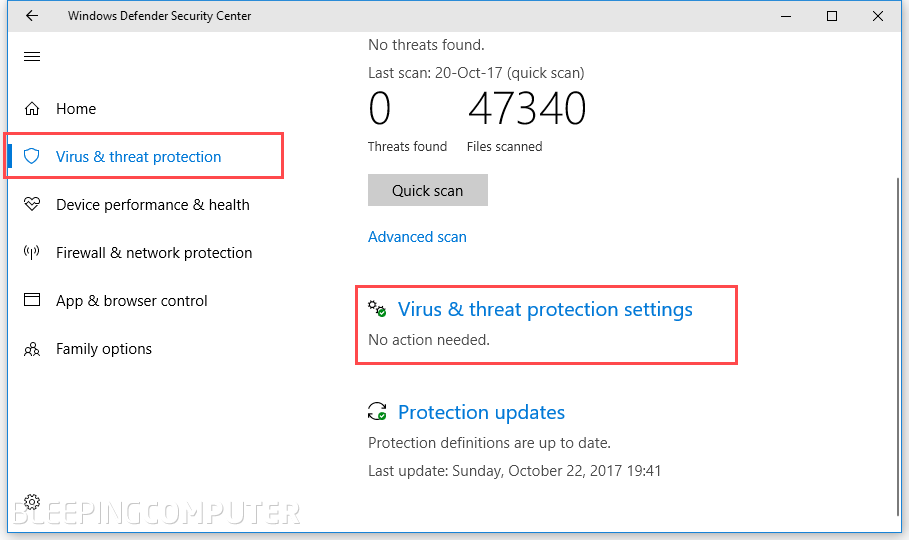
Step 3
Scroll down on this page and locate the "Controlled folder access" section. To enable the feature, just click the On/Off toggle.
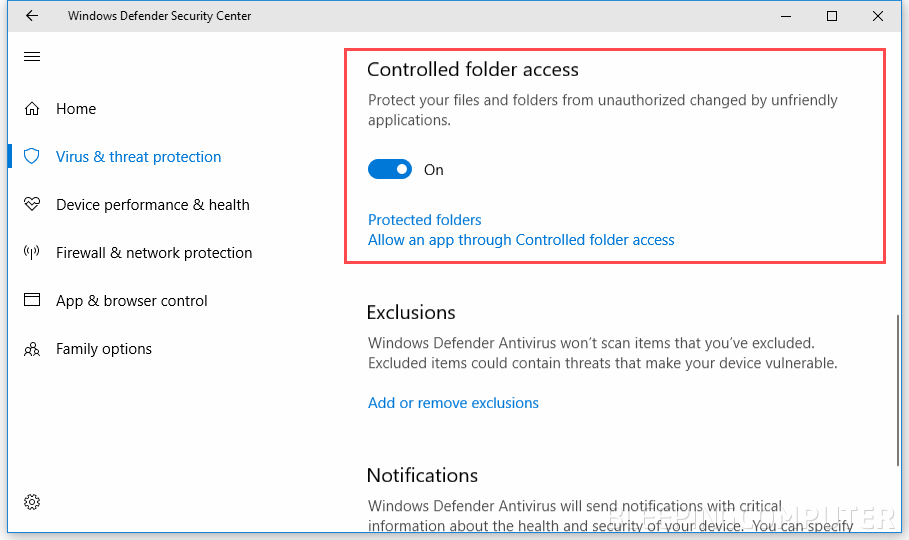
Step 4
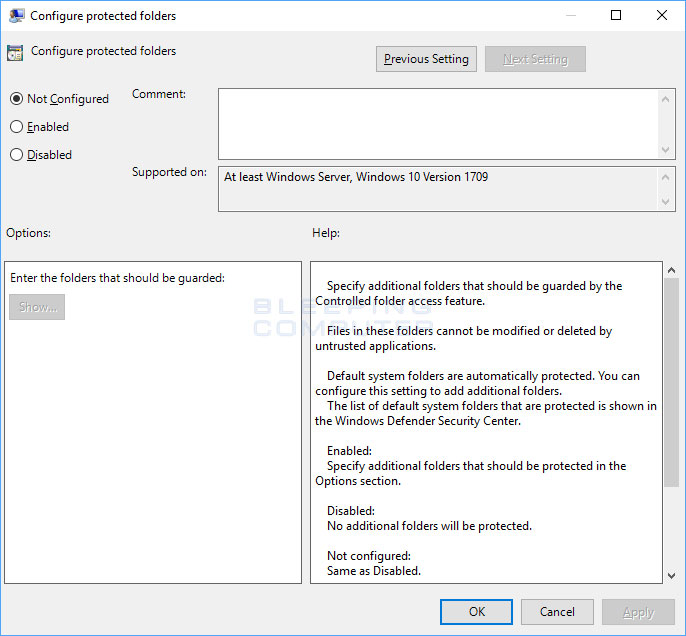
First thing first, select the "Protected folders" sub-option and add all the folders you want to restrict access to.
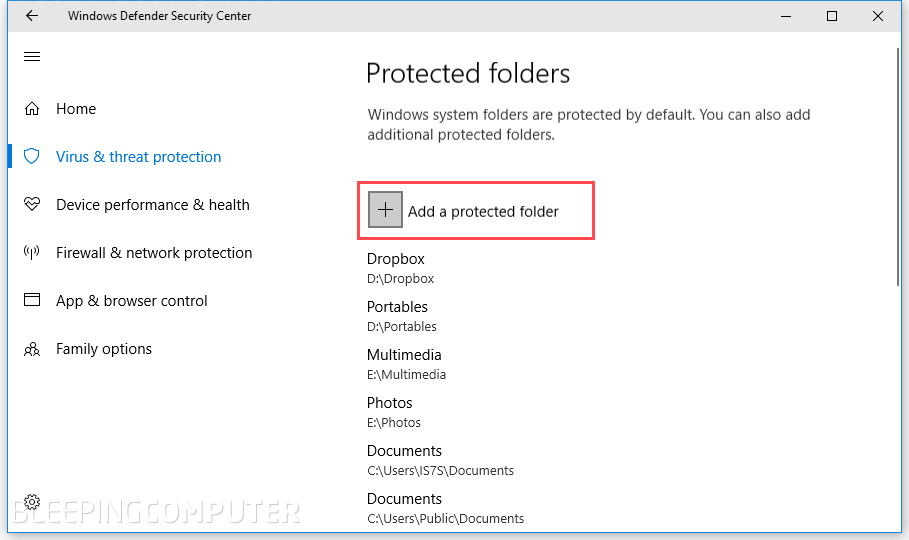
Step 5
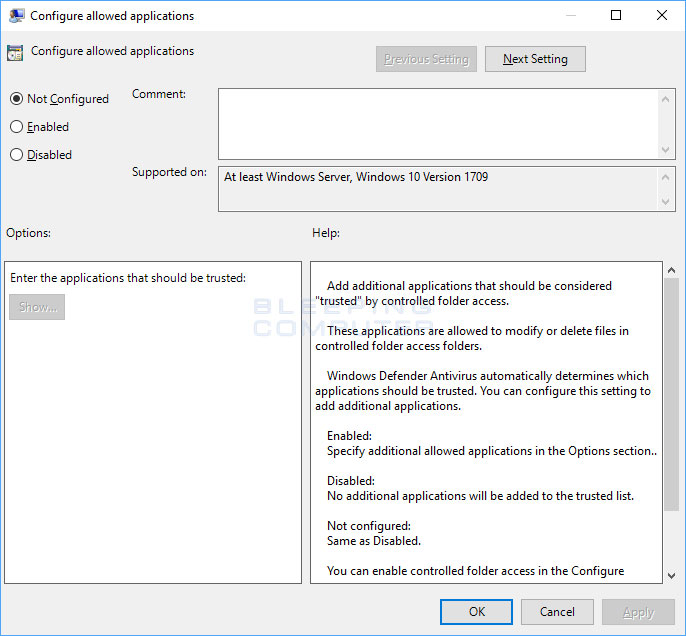
Now it's time to select the second option named "Allow an app through Controlled folder access." This option will whitelist the apps that are allowed to access, edit, create or remove files from protected folders.
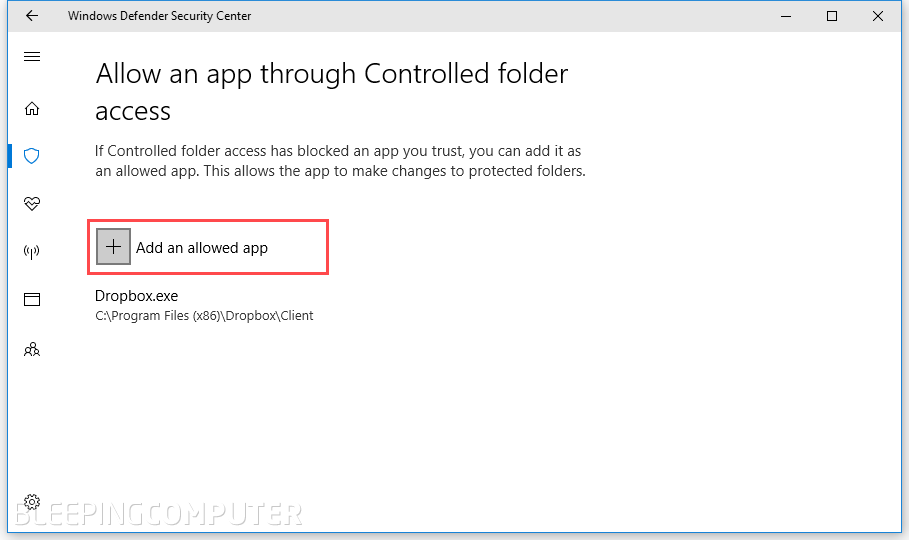
Other ways to enable Controlled Folder Access
Besides the instructions above, there are two other ways to enable Controlled Folder Access. The easiest way is by running the following Powershell command.
Set-MpPreference -EnableControlledFolderAccess EnabledTo disable the feature, just run the same command, but with the "Disabled" argument.
In addition, system administrators in large organizations can use the Group Policy Management Console to enable the feature for users across a local network.
Step 2: In the Group Policy Management Editor go to Computer configuration.
Step 3: Click Policies then Administrative templates.
Step 4: Expand the tree to Windows components ⋙ Windows Defender Antivirus ⋙ Windows Defender Exploit Guard ⋙ Controlled folder access.
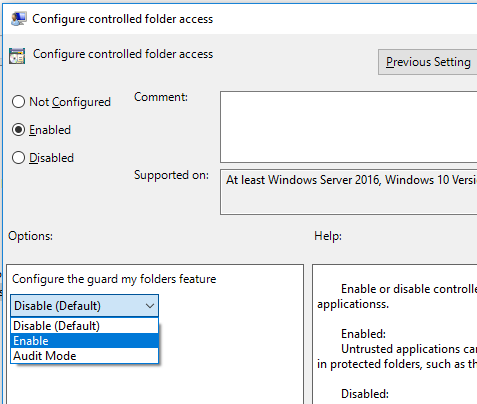
Step 5: Double-click the Configure Controlled folder access setting and set the option to Enabled.
You can also use Group Policy to configure allowed applications and protected folders. This allows a a system administrator to easily push out lists of whitelisted programs and protected folders to every computer on a domain.
|
|
|
When everything's up and running, if an unauthorized program tries to edit one of the files located in a Controlled access folder, users will get a warning through the Windows Notifications sidebar, while the app trying to make the edit will get stopped dead in its tracks. Further, Windows Defender will also record the unauthorized access in the Windows event log (with this dependency installed).
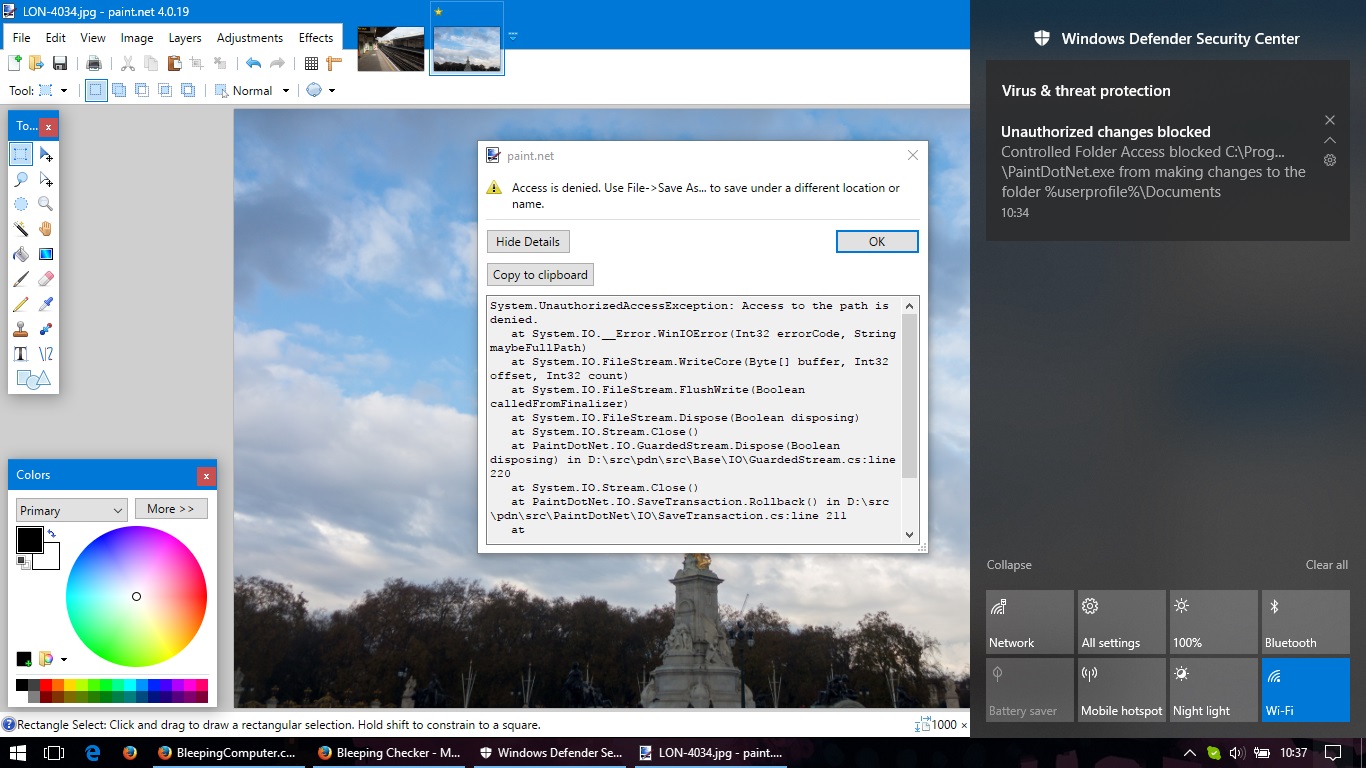
In order for Control Folder Access to work, though, real-time protection must be enabled in Windows Defender. Bleeping Computer has reached out to Microsoft about the possibility of offering Controlled Folder Access as a separate feature, and a company spokesperson said there are no such plans for the immediate future.
Testing Controlled Folder Access against Ransomware
BleepingComputer has tested Controlled Folder Access against ransomware samples that include the Asasin Locky variant, the x1881 CryptoMix variant, the Comrade HiddenTear variant, and the Wyvern BTCWare variant. The good news is that Controlled Folder Access achieved what it was designed to do; successfully block ransomware from encrypting files located in protected folders.
The bad news is that while your protected folders are safe, other non-protected folders will still be encrypted, ransom notes will still be displayed, and other behavior will still continue.
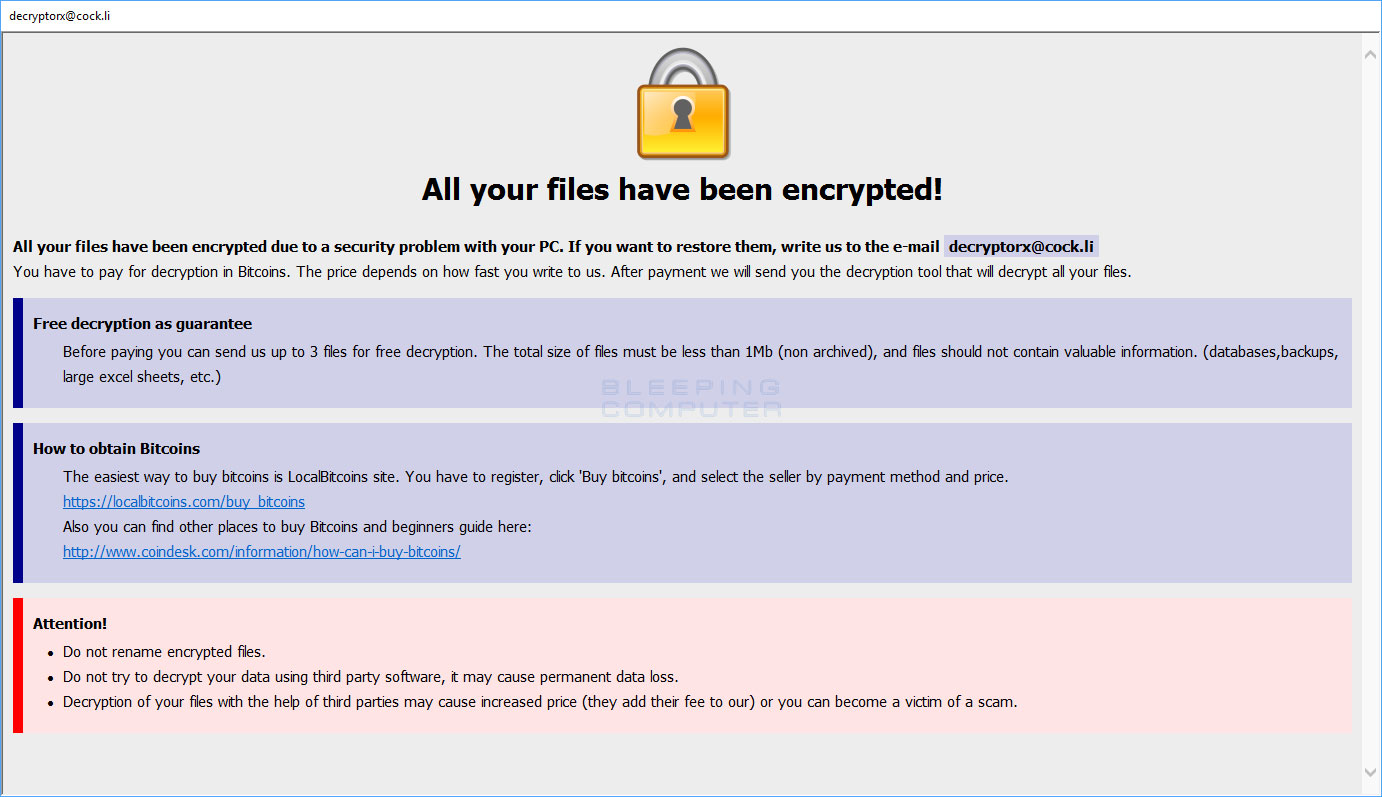
This is because Controlled Folder Access is not designed to terminate detected ransomware, but rather protect a folder from ANY unauthorized modifications. This includes any program not in a white list, which could be 3rd party text editors, word processing applications, or photo editing programs.
Also, while testing Controlled Folder Access, an interesting side-effect was discovered when folders are whitelisted in Windows Defender. When executables are located in a whitelisted folder and attempt to modify a file in a protected folder, Controlled Folder Access will block the modification, but not display a toast alert notifying you that the program was blocked.
While BleepingComputer highly recommend that everyone use Controlled Folder Access, it should not be considered a full-fledged anti-ransomware feature, but more like a data protection feature. While in some ways this is the same, in many ways it is different.
Additional reporting by Lawrence Abrams

.jpg)
Comments
Occasional - 6 years ago
Thanks CC. Nice step-by-step guide. Hope to see more takes on how well this works, which folders you should or shouldn't include, side effects, etc.... Especially interested in how well this plays with others (browsers, apps, mixed OS networks...).
dwmc2 - 6 years ago
When activated and some app tries to make a change (e.g., you use Windows Fax & Scan to scan a document and then try to Save As, a pop-up appears with the notification that Defender prevented the change by some app. The path of the app is abbreviated and the popup doesn't stay around long, but it's also in your notifications. The trick is adding that app by name to the list of allowed apps - non-trivial. I like the protection, but it seems like MS could have exempted more standard utilities.
Other fall creator's update issues that may or may not be related, such as errors in pickerhost.exe - the Windows file selector - and connecting an android phone via usb.
campuscodi - 6 years ago
Yes. The path abbreviation is the biggest problem. Especially for people running portable apps where you have no idea where the actual executable is.
Uncle bob - 6 years ago
Good article. I wonder how long it would have taken me to find out about it, if it weren't for bleepingcomputer. Not a total solution. But, another arrow in the quiver and should make things harder for the bad guys.
Zinc64 - 6 years ago
Not available if you use 3rd party Anti-virus?
dwmc2 - 6 years ago
No. It is specifically a part of Windows Defender (Microsoft's AV)
GeekB4GeekwasCool - 6 years ago
ARGH not available with 3rd party, sigh
Lawrence Abrams - 6 years ago
Agreed. I was disappointed in this as well. When I spoke to the Defender team about this I was told that controlled folder access requires the real-time protection component of Defender.
Honestly, defender did such a good job detecting the ransomware samples at it that I am not against using it. Still need to evaluate it against other types of malware, especially adware, which is so common these days.
Taxprorio - 6 years ago
My only problem with the new feature is that once you add a folder to the list of controlled folders, there doesn't seem to be a way to remove it.... Caveat Emptor!
I had to turn it off, until they put in a "remove" option....
compmend - 6 years ago
This doesn't apply to the pre-defined list only the items you add in manually, In the list of "Protected Folders", you can single left click on the folder you want to remove and a button will appear below the selected item, right-aligned that says "remove" on it. Click the button and confirm you want to delete the item and it will be gone.
PeeJay1935 - 6 years ago
I have tried to turn on "Controlled folder access" as per your instructions but the "On/Off toggle" is at "Off" and is greyed out and can't be changed,
I am using Windows 10 Home edition v1709 OS build 06299.192
Is "Controlled folder access" only available in the Pro edition or should it also be in Home? If so, how can I get it to activate?
dwmc2 - 6 years ago
Controlled folder access is definitely available in Windows 10 Home Edition.
dwmc2 - 6 years ago
Controlled folder access is definitely available in Windows 10 Home Edition.
dwmc2 - 6 years ago
Controlled folder access is definitely available in Windows 10 Home Edition.
dwmc2 - 6 years ago
https://docs.microsoft.com/en-us/windows/threat-protection/windows-defender-exploit-guard/enable-controlled-folders-exploit-guard
The link above is the official word on how to enable folder protection. Note that it is enabled through Windows Defender. If you don't have Windows Defender running you need to do that first. If you are using some other AV product, that may be inhibiting the Folder Protection function.
bromberg - 6 years ago
I think that was my problem: as soon as I stopped Malwarebytes and started Defender I saw the CONTROL FOLDER ACCESS option in SETTINGS (it was grayed out but at least it appeared). Still don't know how to tell whether the PowerShell command described in the article worked (unless not issuing an error message after its' execution means it worked?!?).
Dan
bromberg - 6 years ago
I have Windows 10 Pro v1709 and don't see a CONTROLLED FOLDER ACCESS option under the DEFENDER panels as you described. Are you certain it is still available?
Dan
campuscodi - 6 years ago
Yes. The feature is (still) active.
bromberg - 6 years ago
Also, I followed your advice about running it in PowerShell by issuing this command:
Set-MpPreference -EnableControlledFolderAccess Enabled
The first time PS complained about not being authorized but then I ran PS as authorized and it no longer complained, but how do I know my "controlled folder access" has truly taken effect?
Dan
nohubris - 5 years ago
Why would MS make such a defined way for protection against RWare yet then tell you to add just about anything you'd like to the ignore page.
The majority of people are not smart enough to know what is ok to open access to and what is not. WTF!
rugbydah - 5 years ago
I have a pickerhost.exe issue in that it will not allow me to save my scanned in files to one of my folders. I have followed your instructions, but I am unable to locate my scanner file to attached it to protected folders. Any advice?
PDN - 4 years ago
Until I have a chance to remove I will leave the feature off -1903