On Tuesday, an offshoot of Anonymous, called AntiSec, claimed to have purloined a list of 12 million iOS unique device identifiers, or UDIDs, along with various bits of user data connected to those UDIDs. While the revelation raised the specter of privacy violations, it became clear that users have plenty of questions about what kind of information can and cannot be gleaned from one's iPhone or iPad UDID. Here, we explain what exactly a UDID is, how it is used, why Apple deprecated its use by developers, and why the privacy fears aren't entirely unfounded.
What is a UDID?
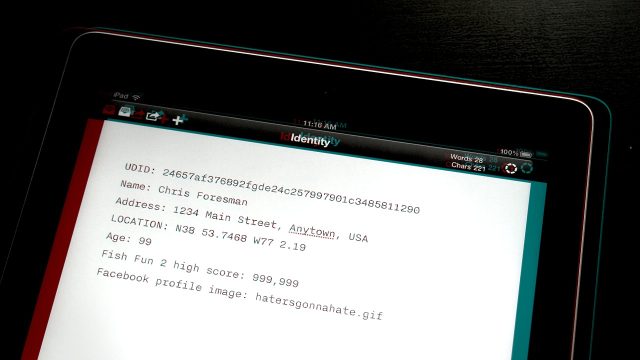
A UDID is a 40 character string of letters and numbers, sort of like a serial number, and uniquely identifies a particular iOS device, including iPhones, iPads, and iPod touches. The alphanumeric code looks completely random to people, but it is actually based on various hardware characteristics. Like a serial number, each iOS device has a UDID that refers to only that specific device. You can see your own device's UDID by going into iTunes and clicking on your device's serial number on its sync screen.
What is a UDID used for?
Since a UDID can be used as a reference to a specific iOS device, it can be used to connect other kinds of data to that device. For instance, UDIDs are used to connect a device to an iOS Developer Account, which allows that device to install and test apps written by that developer before their public release. Connecting the UDID to a developer account also allows that device to install beta releases of iOS for testing.
Apple also uses the UDID to connect devices to a user's Apple ID. This allows those devices to automatically download and install apps purchased on the App Store, or music purchased from iTunes. It allows a user's device to upload a high score to Game Center. It also allows Apple to route push notifications and iMessages to the correct device.
(It's worth noting that a bug in iMessages allowed devices that had been stolen or sold, and otherwise wiped of data, to still receive messages connected to that UDID. Apple has never publicly confirmed that the bug has been fixed.)
In the early days of iOS apps, UDIDs were also used by third-party developers and ad networks to collect data about users. The UDID could be used as a sort of token to correlate certain information about a user, such as location, app usage habits, and more, in order to send targeted ads. Developers often used the UDIDs to connect to pre-Game Center social networks like OpenFeint and Plus+.
Why did Apple deprecate the use of UDIDs by developers?
The UDID could be used as a sort of "anonymized" token. However, many developers connected a UDID with users' real names, user names, passwords, location, or other data. While the UDID alone would be of little use to hackers or identity thieves, network snoopers could correlate these UDIDs with other data gleaned from multiple apps, which privacy advocates believe is plenty to home in on a particular person.
Indeed, despite the promise of "anonymized" data, computer scientists have repeatedly demonstrated that it's possible to "de-anonymize" or "re-identify" individuals from large, anonymized datasets, including Netflix rental histories and databases of tweets. Director of Harvard University's Data Privacy Lab, Dr. Latanya Sweeney, showed as part of her graduate research in 2000 that it was possible to uniquely identify 87 percent of Americans using just a ZIP code, birthdate, and sex.
In October 2010, Bucknell University Assistant Director of Information Security and Networking Eric Smith released a paper showing that a large percentage of apps were transmitting UDIDs along with other personally identifying information.
"For example, Amazon's application communicates the logged-in user's real name in plain text, along with the UDID, permitting both Amazon.com and network eavesdroppers to easily match a phone's UDID with the name of the phone's owner. The CBS News application transmits both the UDID and the iPhone device’s user-assigned name, which frequently contains the owner’s real name," Smith's report noted.
That data could be correlated by companies and shared or sold to "unintended customers such as advertisers, spouses, divorce lawyers, debt collectors, or industrial spies," according to Smith. Hackers and identity thieves could very well do the same thing.
The revelation led to a class-action lawsuit, which ultimately ended up being dismissed. However, Apple apparently decided to play it safe, so it deprecated the use of UDIDs in iOS 5, released in October 2011. Developers were directed to generate a unique identifier that is only accessible by a single app when needed. Furthermore, apps that attempt to access a device's UDID are now rejected from the App Store. Apple has also been more proactive about requiring apps that collect user data to have explicit user permission, and is adding some additional checks in iOS 6 to limit access to certain information stored on iOS devices.
So why are UDIDs still a privacy concern?
The recent posting of over 1 million UDIDs by AntiSec—with the promise that 11 million more may be released in the future—could still potentially result in privacy concerns. Despite the fact that Apple has deprecated the use of UDIDs, some developers have not scrubbed UDIDs from their databases.
In particular, security consultant Aldo Cortesi demonstrated last year that it is relatively trivial to de-anonymize a UDID using OpenFeint's Web-based API, which still contains personal information linked to UDIDs. Among the data that Cortesi collected from OpenFeint using his own UDID was his latitude and longitude, the last game he played, his account name, and his Facebook profile picture URL.
"I want to stress that the problem here is not primarily with OpenFeint," Cortesi wrote. "By designing an API to expose UDIDs and encouraging developers to use it, Apple has ensured that there are literally thousands of databases linking UDIDs to sensitive user information on the 'Net. A leak from any one of these—or worse, a large-scale de-anonymization like the OpenFeint one—inevitably has serious consequences for user privacy."
Other developers we spoke to agreed that the past use of UDIDs has created a potential for privacy invasion.
"By itself, a UDID contains no more personal information than any given 'username,'" developer Steven Troughton-Smith told Ars. "The security issues arise when third parties have used this UDID as an access token for your account on their service, which is incredibly dumb and insecure; it's a bit like allowing anybody with your username to log in as you without a password. Some of these services—like the various game networks—might also have your Twitter and Facebook credentials stored, depending on what you've given them in the past, to cross-post to services. Or [they are] also keeping whatever other personal data you have given them.
"The fact that this is a UDID isn't important; it could have been a username, phone number, or address book contact, or device serial number," Troughton-Smith said. "The problem comes in them storing all this other information with no other means of authenticating you or securing the data."
Seemingly innocuous bits of information could lead to a full-blown identity hack, as recently experienced by Wired Senior Editor Mat Honan. Using just a few bits of data gleaned from his Amazon account, a hacker was able to take over his iCloud account, access his e-mail and Twitter accounts, and wipe the data from his iPhone and MacBook Pro.
"Further leaks of UDID lists can be used to cross reference users," developer Jonathan Wight told Ars. "That's my main fear—once more leaks are made, you can find UDIDs that exist in leaked tables. And if those leaked tables contain further info, you'll start to develop a fuller picture of the user."
A more specific concern is that the data released by AntiSec was claimed to have been taken from the hacked laptop of an FBI agent.
"If the FBI could gain access to other systems, it could gather more personal information," developer Brent Simmons told Ars. "I don't know enough about the technical or legal details to suggest how possible or likely this is, but I'm massively uncomfortable with the idea of any government agency collecting private information on a mass scale."
AntiSec has so far refused to offer any proof that the data was in fact obtained from the FBI. For its part, the FBI says it has no knowledge of any such data collection and has issued vehement denials of AntiSec's claims on Twitter.
"The FBI is aware of published reports alleging that an FBI laptop was compromised and private data regarding Apple UDIDs was exposed. At this time, there is no evidence indicating that an FBI laptop was compromised or that the FBI either sought or obtained this data," the agency said in a statement.
Sources speaking to The Wall Street Journal claimed in June that Apple was developing a system to replace UDIDs with a more "privacy-conscious" system within iOS itself. But Troughton-Smith explained that Apple can't really "fix" the fact that UDIDs were previously used to collect and correlate user data. Privacy concerns will continue to exist as long as that data is stored somewhere outside a user's control. For the time being, however, there are steps users can take to secure their online data as much as possible.
reader comments
36