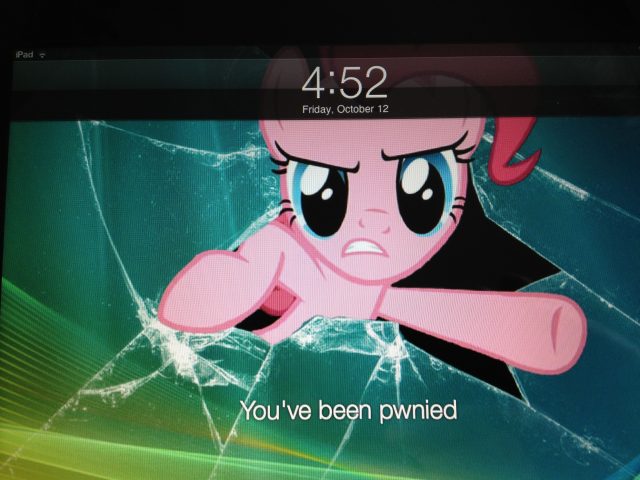
Apple recently released the latest version of Configurator, the company's management software for iOS devices, for download in the Mac App Store. Configurator version 1.2 is intended to give organizations a way to mass-configure iPads, iPhones, and even iPods with applications, settings, and security policies. It's also, as it turns out, the perfect tool to prank a teenage son, teaching him the hazards of leaving his iPad unattended and of interrupting conference calls with extended drum solos.
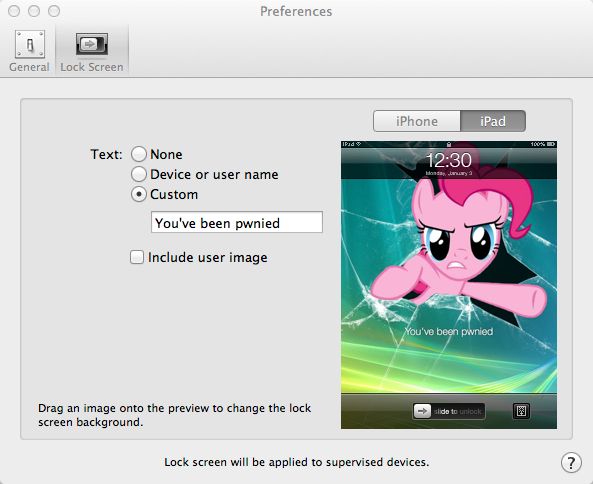
Configurator version 1.2 is enhanced to take advantage of the enterprise management features in iOS 6. It provides all the policy configuration muscle Apple gives to mobile device management tool developers with its management interfaces, in a free Mac OS X application. That includes the ability to lock down the lock screen, put a device into "app lock" mode, making it boot straight into an application, and blocking users' access to the rest of iOS's features. All those features let you turn a device into a secure wireless kiosk, a point-of sale system, or (as I did to my son's iPad) a dedicated My Little Pony Ruckus Reader platform with an appropriately themed lock screen.
Of course, I backed all his stuff up first. I'm not that evil.
From iPad to iPwnie in three easy steps
There are two distinct levels of management control in iOS 6—supervised and unsupervised devices. Unsupervised device management is best for BYOD situations; it can be configured without being overly intrusive. Profiles set up this way can be overlaid on existing user settings, and can even be set to automatically expire after a specific period. Admins can give contractors access to resources for the length of a specific project without having to get a hold of their device to revoke it afterward, or give students access for the length of a specific class.
Supervised devices, on the other hand, require a re-install of iOS that throws additional management switches on and gives the administrator more control over configuration. Prior to iOS 6, supervised mode was only available for the iPad. Now, as we noted in our report on iOS 6's enterprise features, it's available for any iOS device.
Supervised mode can prevent the user from changing some or all of the device's configuration, selectively shut off features, prevent users from removing apps, and limit the types of content the device can download or use. It also allows administrators to "app lock" the device, so that it boots up directly into a specific application—with no way for the user to exit from it.
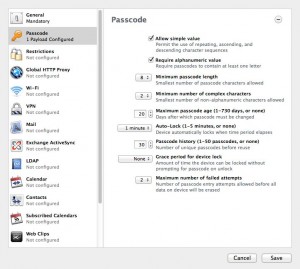
Supervised mode comes at an administrative price, however. While unsupervised profiles can be set up to allow users to enter their usernames and passwords for features that require authentication, these need to be hard-coded in for devices put in supervised mode. Of course, the level of control from supervised mode is exactly what many companies want for their devices. Most devices that organizations will put in supervised mode will likely be used by multiple people, and won't need to have personalized e-mail or other settings.
Configurator's interface is broken into three views. The "Prepare" view is intended for initial provisioning of devices—setting them up with initial policies in either supervised or unsupervised mode and installing applications. You can also back up one device after it's been completely configured, and use the backup as an image to provision other devices.
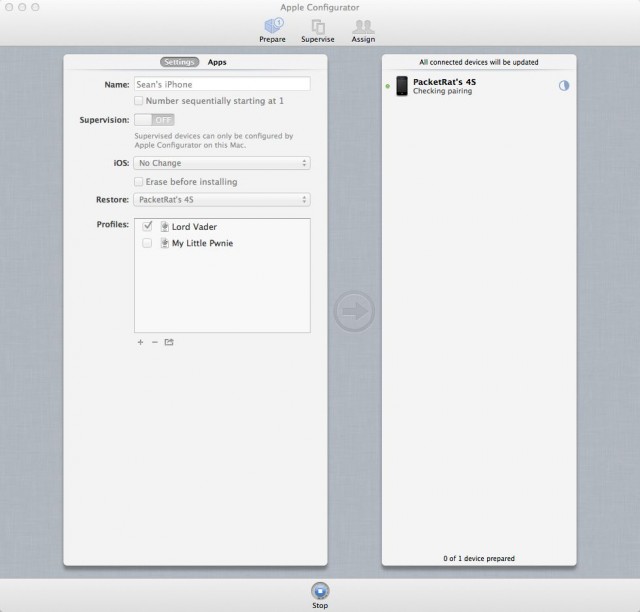
The "Supervise" view is intended to manage supervised devices after they're configured. Admins can assign devices to groups so additional policies can be applied in batches. And this is where you can put devices into "app lock."
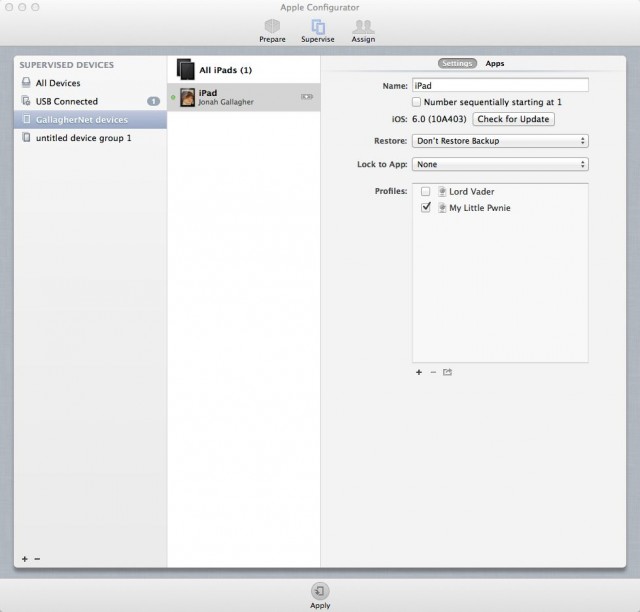
And finally, the "Assign" view is for checking out specific devices to users and managing their personalized application data. When you check in a device, it backs up the user's data files to Configurator's library, so that they can be re-installed the next time the user is issued the device.
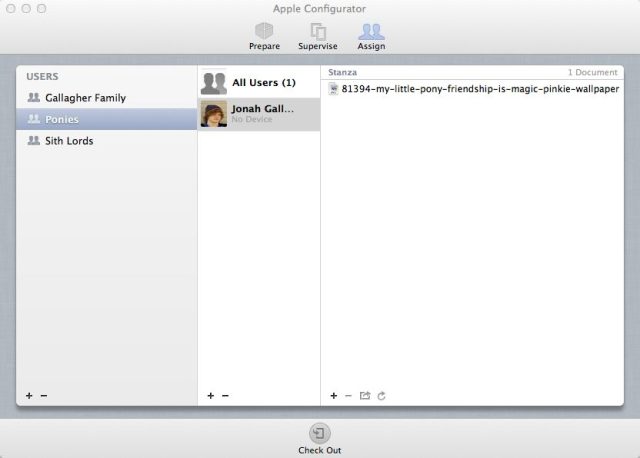
Some of the more general configuration settings for devices—such as lock screen graphics and customized text for supervised devices—are set up in Configurator's preferences menu.
Both Prepare and Supervise allow you to create new policies or edit existing ones, and assign applications to be deployed. You can also import or export profile information (in an XML format with a .mobileconfig file extension) within both views. So one administrator can create a set of profiles to be distributed to anyone setting up iOS devices. They can also be imported and sent out to devices over-the-air by MDM tools via Apple's Push Notification Service, as described in Apple's MDM integration documentation (PDF here). Sadly, there's no over-the-air update integration in Configurator itself, but I suppose some things can't be free.
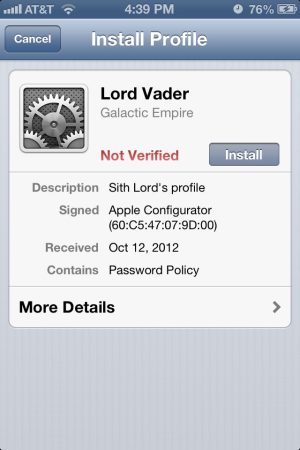
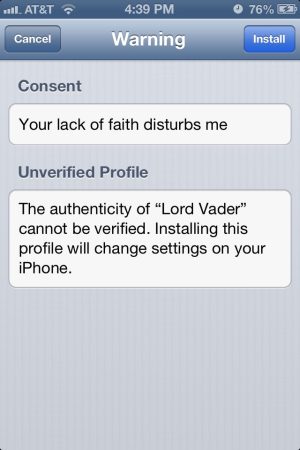
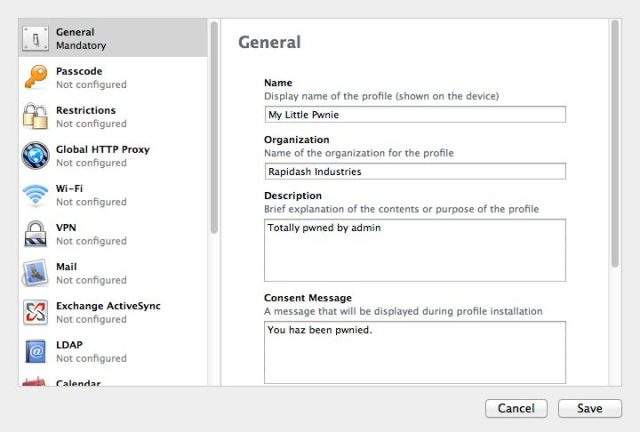
Configurator's profile editing interface creates a "package" for each component of the configuration an administrator sets. The first set of data for a profile is general information for the header of the profile, including its name, a description, and the consent message that it displays when sent to the device. Once you build profiles, you can deploy them to groups of devices—up to 30 at a time, hooked up by USB hubs. The profiles can be exported as well, and sent through MDM tools for remote policy changes.
[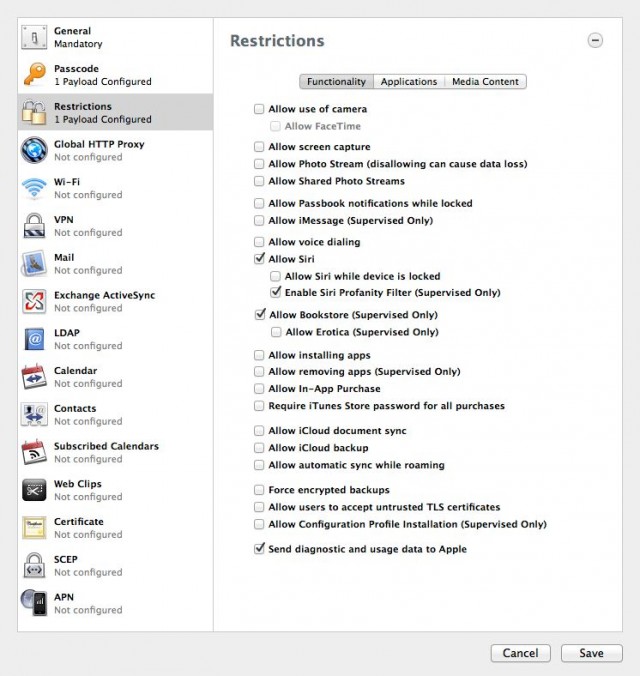
Configurator now allows administrators to enable and lock Siri's profanity filter, to prevent the app from being persuaded to parrot dirty words. Of course, you can always block Siri altogether. You can also now block (or allow) iOS's Game Center. Configurator policies can also block access to the iBooks bookstore in supervised mode, or just block anything in the store labeled as "erotica." There are also some features that don't require "supervised mode" that have been added to the policy toolbox. FaceTime and iCloud features such as document sync and Photo Stream can be disabled by policies, for example. In Photo Stream, you can lock down the feature entirely, or just prevent users from pushing photos to shared Photo Streams.
Configurator 1.2 exposes all of the new supervised mode functionality, in addition to new feature and security settings that can be configured without having to get that medieval on the user. For example, Supervised mode isn't required for many of the other new policy controls in iOS 6. FaceTime and iCloud features such as document sync and Photo Stream can be disabled by policies, for example; in Photo Stream, you can lock down the feature entirely, or just prevent users from pushing photos to shared Photo Streams.
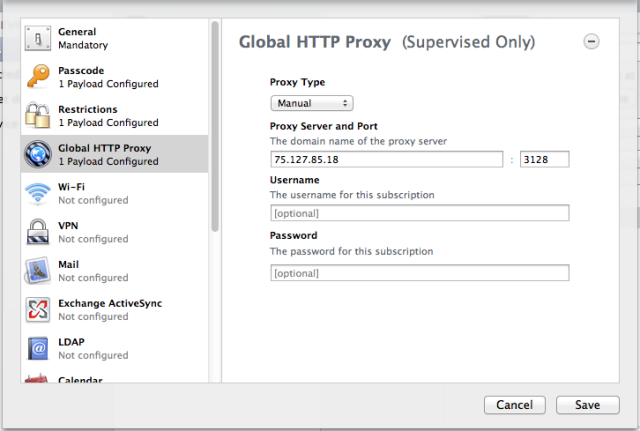
The highest level of control achievable through supervised mode is "app lock" mode. This isn't set in the policy profile itself, but as a switch passed to iOS 6's "Guided Access" feature when docked. You can create a backup of an app-locked device to use as a template, but there's no way to remotely turn app lock on or off over-the-air—which might be a good thing, at least for my son.
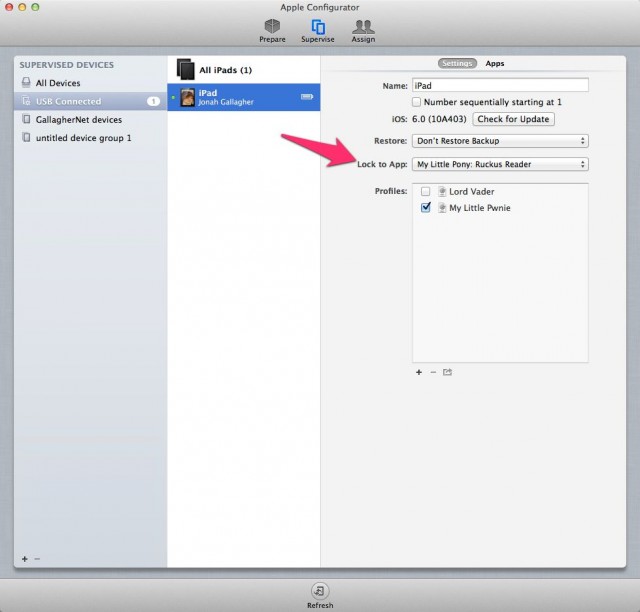
Pwning complete?
Configurator would be even more useful if Apple provided a way for admins to connect it directly into Apple's Push Notification service to do over-the-air configuration. But then, that sort of Configurator would not be a free App Store download—it would require a back-end database of devices and other features that would essentially turn it into an MDM platform. Apple apparently isn't interested in doing that (or at least it hasn't hinted at it) much to the relief of MDM vendors who support iOS devices.
But while Configurator isn't a substitute for an MDM system in larger organizations, it does provide a way for administrators to quickly build policies to be used in MDM environments. Even without remote management, Configurator is probably all many small to mid-sized organizations will need to ensure that "bring your own" iOS devices are configured correctly for e-mail and basic security, or to manage a pool of company-owned devices being issued to employees or students for specific tasks.
At a minimum, Configurator is certainly enough for individuals who want an easier way to lock down their own devices and protect their mobile data. As for its value as family entertainment, the look on my son's face when he turned on his iPad was priceless.
reader comments
59