Although Google’s Android dominates the worldwide smartphone market, the CIA concentrated on Apple’s iOS because of its popularity among global elites, WikiLeaks reports.
The huge trove of leaked CIA documents, codenamed “Vault 7” and released Tuesday by WikiLeaks, reveals that the CIA formed a special unit called the Mobile Development Branch (MDB) to infect smartphones. And within that unit, Apple’s iOS was a prime target.
According to WikiLeaks, the CIA’s MDB developed or exploited a range of hacks, vulnerabilities and even specialized malware to turn iPhones and iPads into spying devices. Compromised iPhones and iPads can track users’ conversations, texts, geolocations and even remotely turn on the camera and microphone.
WikiLeaks’ introduction to the giant cache of leaked CIA files — which at 8,761 documents (so far) is claimed to be the largest in history — says that Apple’s devices were of particular interest to the U.S. spy agency.
Despite iPhone’s minority share (14.5%) of the global smart phone market in 2016, a specialized unit in the CIA’s Mobile Development Branch produces malware to infest, control and exfiltrate data from iPhones and other Apple products running iOS, such as iPads. CIA’s arsenal includes numerous local and remote “zero days” developed by CIA or obtained from GCHQ, NSA, FBI or purchased from cyber arms contractors such as Baitshop. The disproportionate focus on iOS may be explained by the popularity of the iPhone among social, political, diplomatic and business elites.
So-called zero-day exploits are software security holes that are unknown to the software’s publisher — in this case, Apple. They are called “zero day” because they are exploited before they are known, giving the publisher “zero days” to fix it or advise on a workaround.
The CIA’s iOS Triage Process
One of the leaked documents details how the CIA tries to break into new versions of iOS as soon as they get released by Apple. Titled “iOS Triage Process,” it lays out the step-by-step process for cracking a new version of iOS using hacking tools such as Saline, Adderall and Nightvision.
According to another classified document published by WikiLeaks, which serves as a kind of cheat sheet for decoding the CIA’s iOS hacking operations, Adderall is a “tool to pull IPSW files and kernel cache from devices,” while NightVision is a “utility to read kernel memory and get/put files as .tbz.”
Weaponized exploits
As well as various zero-day exploits, WikiLeaks says the MDB’s “hacking arsenal” includes malware, viruses and trojans. These “weaponized” exploits allow the CIA (or anyone in possession of the malicious code) to “infiltrate, take control of, and exfiltrate” an iPhone or iPad. In other words, the CIA is able to take control of a device, tap into its guts, and extract communications and data.
The CIA’s capabilities are said to include capturing voice and text communications, identifying the user’s precise geolocation, and turning devices into “covert microphones” by activating the mic and/or camera.
The extra good news is that the CIA’s exploits are said to have already been widely leaked and are circulating among “former U.S. government hackers and contractors.” (That’s how WikiLeaks got hold of the material.)
It’s not clear just how widely circulated the spy agency’s hacking tools have been, but anyone in possession of the code has “the entire hacking capacity of the CIA.”
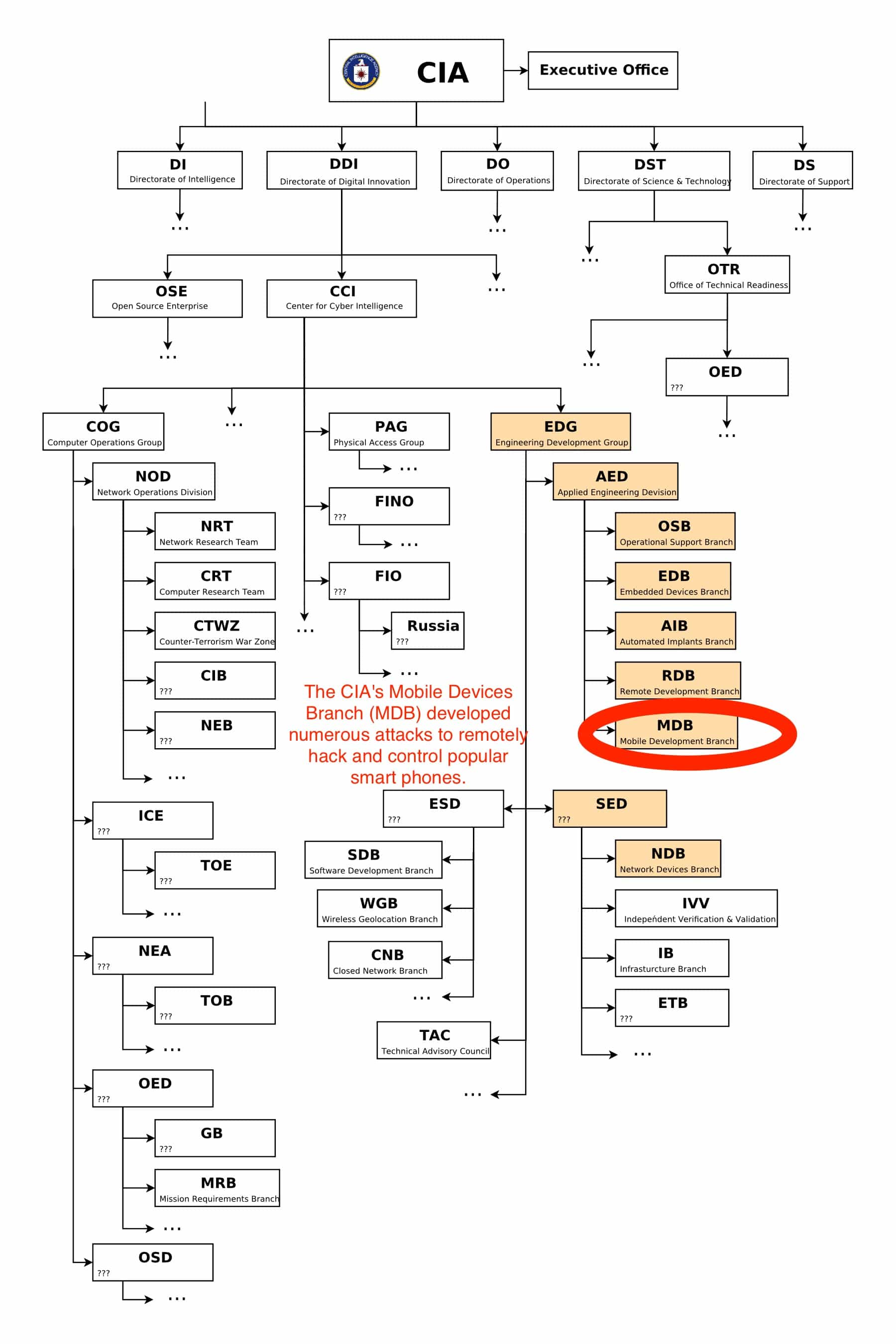
Photo: WikiLeaks


