This article is more than 1 year old
Apple blocks comms-snooping malware
Leaked developer certificate revoked, protection updated
Apple has moved to thwart a malware attack that used a legitimate – probably hijacked – developer certificate, by revoking the cert.
Check Point wrote up the malware last week, calling “OSX/Dok” “the first major scale malware to target OSX users via a coordinated email phishing campaign”.
A hapless user who okayed all the stages of infection would end up having all their communications snooped - even HTTPS sessions encrypted with SSL.
The malware installation process included a legitimate-looking “your computer has a security problem” window that opened on top of all other windows, which Check Point captured:
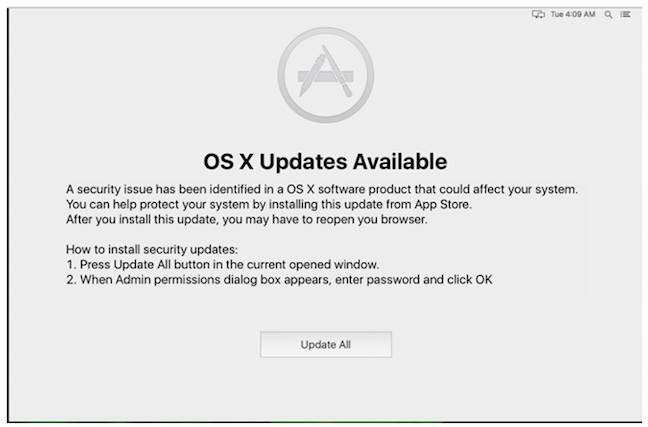
The fake nagware dialogue
If a user relents and okays the dialogue, the malware gets admin privileges, installs the Brew package manager, installs Tor and SOCAT, and forces the user's connections through a proxy for snooping. The traffic interception is supported by the malware installing its own CA certificate, using the Comodo name to help it hide in plain sight in the System keychain.
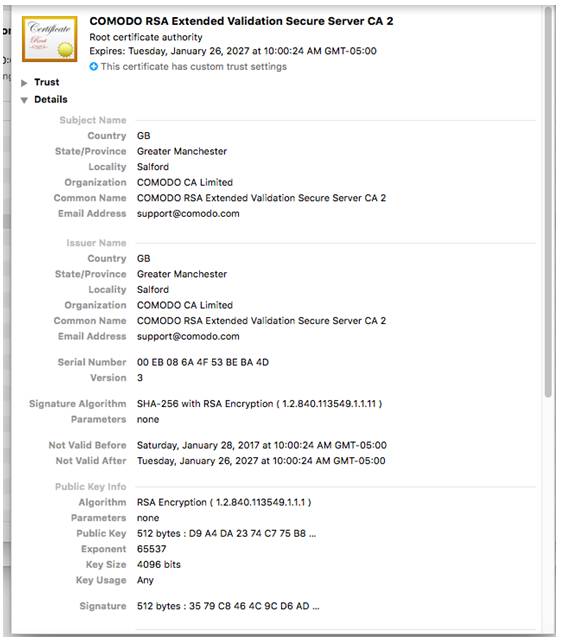
According to Kaspersky's Threatpost, Apple revoked the developer certificate on Sunday, US time, and also dropped an update to its XProtect anti-malware software. ®
