On Friday, Microsoft rolled out an out-of-band security update that patched a major security flaw in the Microsoft Malware Protection Engine (MsMpEng), a core security service part of the Microsoft ecosystem.
The bug, tracked as CVE-2017-8558, affects the x86 emulator included with the Malware Protection Engine and was discovered by Google Project Zero researcher Tavis Ormandy.
According to a technical write-up by Ormandy, the vulnerability allows an attacker to execute code on a user's computer, gain LocalSystem privileges, and take over the victim's PC.
Exploitation is ridiculously simple
Exploiting this flaw is ridiculously simple as it requires an attacker to send a malformed file to the victim via various methods: email, chat message, file download, or trick the victim into accessing a malicious website hosting a weaponized JS file.
There's no user interaction needed, as the MsMpEng will immediately scan new content arriving on the user's PC, and the attacker will gain immediate control over the target's system.
This is a big issue because the Malware Protection Engine has been shipped as a built-in service in all Windows OS versions since Windows 7, and is a core component of a series of Microsoft security products such as Windows Defender, Microsoft Security Essentials, Microsoft Endpoint Protection, Windows Intune Endpoint Protection, and Microsoft Forefront Endpoint Protection. The bug would allow an attacker to crash and bypass these security products.
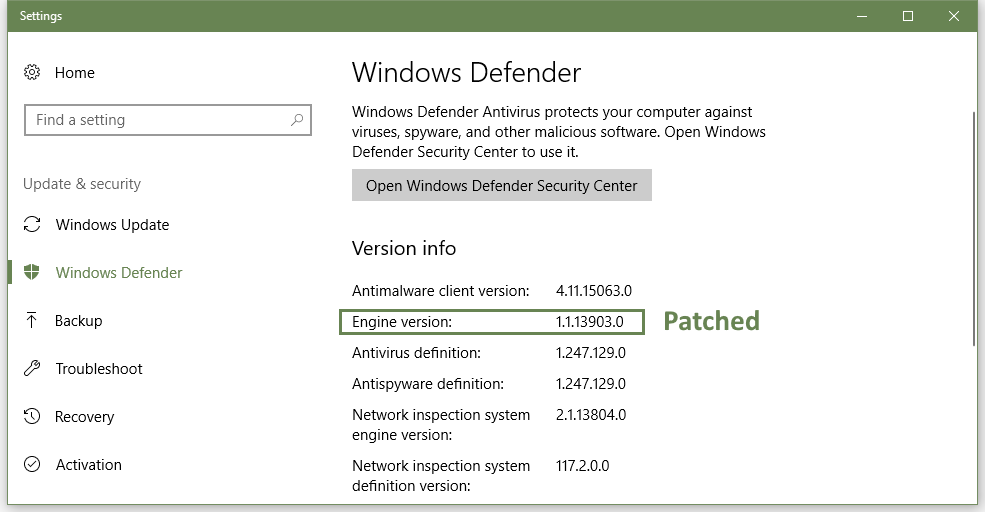
In an advisory, Microsoft said all above-listed products are affected by this issue. The OS maker patched this vulnerability via a silent update to the Malware Protection Engine in version 1.1.13903.0.
The Microsoft Malware Protection Engine silently updates itself, so no user interaction is needed unless the user has specifically blocked updates via update management software.
PoC demo was so dangerous it needed to be encrypted
Ormandy also put together a proof-of-concept file to demo the flaw for Microsoft employees. Showing just how dangerous and easy to exploit this bug was, Ormandy had to encrypt the PoC demo when sending it to Microsoft because he risked crashing Microsoft's email servers the moment the PoC reached their systems.
This is the second time when Ormandy had to encrypt PoC demos. In early May, Ormandy discovered a similar bug, which he described as "crazy bad" and "the worst Windows remote code exec in recent memory."
Three weeks later, one of his colleagues also discovered a series of issues affecting the same MsMpEng component.
Bug would have been worth millions of dollars
All these bugs are dangerous because they allow attackers to crash or bypass security services and take over user's systems. An issue like, if sold on hacking forums, would have pocketed authors millions of dollars, allowing a secret door into any Windows computer on Earth.
Ormandy says he discovered this bug using a technique called fuzzing, which takes random data and feeds it into a program's input to test how the software reacts and exposing bugs.
Over the winter, Ormandy built a tool that ports Windows Defender DLLs to Linux in order to use Linux-based fuzzing tools to test for Windows Defender bugs. He said he specifically put this tool together for testing Windows Defender. Apparently, it worked, exposing issues Microsoft's own fuzzing didn't catch.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now