Mac 'Fruitfly' malware variant still lurking in the wild
The Mac malware, originally discovered back in January, creates a "backdoor" that allows the controller of the malware to take over an entire computer.
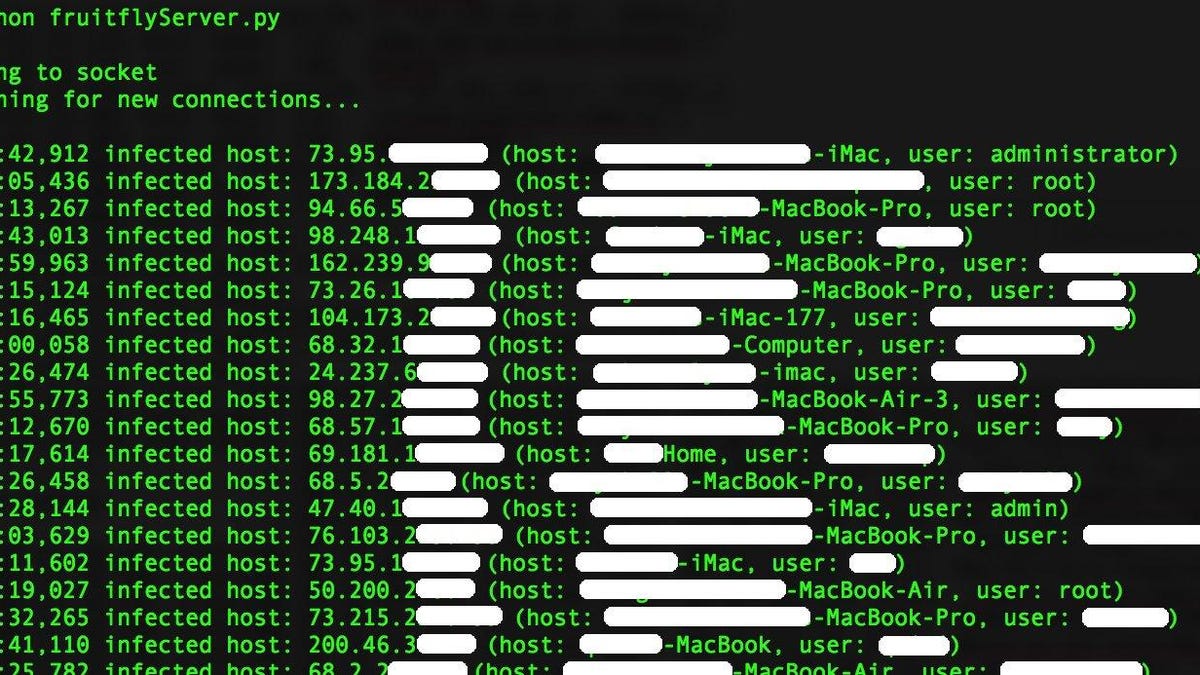
A selection of the computers, their username, and computer's name infected by the Fruitfly malware.
Patrick WardleMac malware is very rare, but the Fruitfly malware first revealed back in January has proven to be both stealthy and mysterious. And now a new variant of the invasive software has been found on hundreds of Macs, according to CNET sister site ZDNet.
The controller of the malware has the capability to remotely take complete control of an infected computer -- files, webcam, screen, keyboard and mouse. That's based on information provided ZDNet's Zack Whittaker by Patrick Wardle, a former NSA hacker and chief security researcher at Synack who has been investigating the malware's capabilities.
Prior to the January revelation of Fruitfly's existence, the malware had apparently existed undetected in the wild for several years "because current Mac security software is often rather ineffective," Wardle explained. While Apple patched to protect against earlier versions of Fruitfly back in January, it's unclear whether Macs running Apple's latest operating systems are vulnerable to the current iteration of the malware.
Wardle's early analysis was that as many as 90 percent of the victims were in the US, according to the article, with no obvious connection between the users. Based on the target victims, however, Wardle thought the malware was run by a single hacker "with the goal to spy on people for perverse reasons" than a nation state attacker. While he wouldn't comment on how many were affected by the malware, he suggested it wasn't widespread.
"I believe the attacker is MIA [missing in action]," Wardle told CNET, "so I don't think people are still being targeted with this malware. Also it likely required user interaction to infect a Mac computer (you'd have to be tricked into downloading/running something). But the malware itself still runs on MacOS," he added.
Wardle is scheduled to speak about the malware at the Black Hat conference in Las Vegas on Wednesday. In the meantime you can read the full ZDNet article here.
Apple did not respond to CNET's request for comment.
Update, 3.15 p.m. ET: Added Wardle's comment to CNET.