Traffic sent to and from Google, Facebook, Apple, and Microsoft was briefly routed through a previously unknown Russian Internet provider Wednesday under circumstances researchers said was suspicious and intentional.
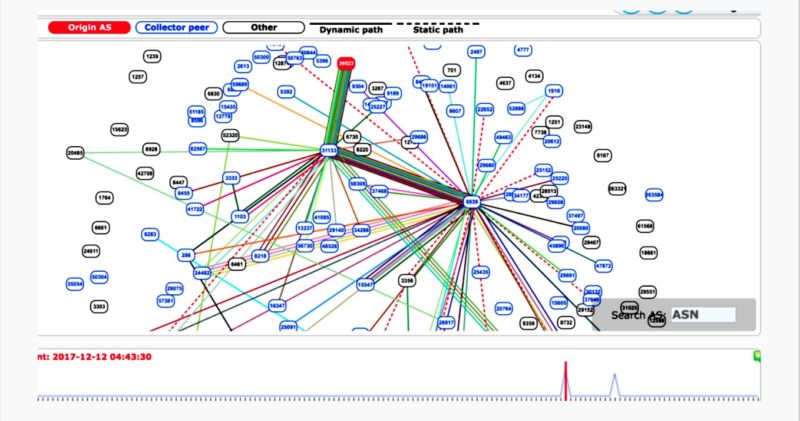
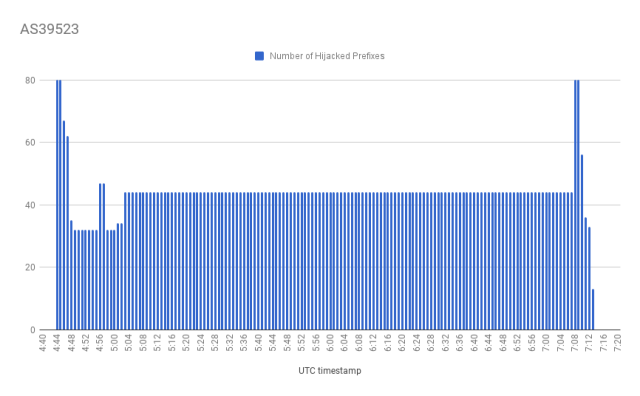
The unexplained incident involving the Internet's Border Gateway Protocol is the latest to raise troubling questions about the trust and reliability of communications sent over the global network. BGP routes large-scale amounts of traffic among Internet backbones, ISPs, and other large networks. But despite the sensitivity and amount of data it controls, BGP's security is often based on trust and word of mouth. Wednesday's event comes eight months after large chunks of network traffic belonging to MasterCard, Visa, and more than two dozen other financial services were briefly routed through a Russian government-controlled telecom, also under suspicious circumstances.According to a blog post published Wednesday by Internet monitoring service BGPMon, the hijack lasted a total of six minutes and affected 80 separate address blocks. It started at 4:43 UTC and continued for three minutes. A second hijacking occurred at 7:07 UTC and also lasted three minutes. Meanwhile, a second monitoring service, Qrator Labs, said the event lasted for two hours, although the number of hijacked address blocks varied from 40 to 80 during that time.
Not just another BGP error
While BGP rerouting events are often the result of human error rather than malicious intent, BGPMon researchers said several things made Wednesday's incident "suspicious." First, the rerouted traffic belonged to some of the most sensitive companies, which—besides Google, Facebook, Apple, and Microsoft—also included Twitch, NTT Communications, and Riot Games. Besides the cherrypicked targets, hijacked IP addresses were broken up into smaller, more specific blocks than those announced by affected companies, an indication the rerouting was "intentional."
"Some of these prefixes don't normally exist, i.e., there was a Google /16 (expected) and all of a sudden a more specific /24 (smaller block)," BGPMon researcher Andree Toonk wrote in an email. "Google did not announce that block, so someone made that up. Normally with BGP configuration errors, we don't see new prefixes."
Companies receive IPv4 addresses in blocks whose sizes are measured by the number following the slash. The smaller the number after the slash, the more addresses are included. A /16 block has about 64,000 usable addresses, while a /24 has only 254. In BGP routing tables, smaller, more specific blocks generally get preference over the larger blocks. Newly announced routes with smaller block sizes also stand a better chance of being picked up by other Internet backbones and ISPs since the route is more attractive.
The rerouting was the result of a so-called autonomous system located in Russia adding entries to BGP tables claiming it was the rightful origin of the 80 affected prefixes. In short order, a variety of autonomous systems started complying with the request. This caused large amounts of traffic sent to and received by the affected companies to pass through the Russian AS 39523 before being sent to its final destination. ISPs that picked up the new route included PJSC MegaFon, Hurricane Electric, Zayo, Nordunet, and Telstra.
Who is AS39523?
Little is currently known about AS39523, the previously unused autonomous system that initiated the hijacking. AS39523 hasn't been active in years, except for one brief BGP incident in August that also involved Google.
It remains unclear what engineers inside AS39523 did with what could be terabytes of data that passed through their servers. Generally, email and Web traffic is encrypted using transport layer security or other schemes. For years, researchers have devised ways to weaken or altogether break such encryption protections or work around them. To accomplish this, they've used attacks with names including Logjam and DROWN. To date, there are no known instances of BGP hijackers successfully decrypting rerouted traffic, but it's also not possible to rule out such feats. At a minimum, the Russian provider could have copied the data and is storing it in case a new crypto attack is discovered in the future.
Wednesday's event is only the latest example of how the Internet's BGP has been abused or misconfigured. The previously mentioned incident in April—in which traffic for Visa, MasterCard, and other financial services passed through a Russian ISP—also appears suspicious. In 2013, researchers documented frequent BGP hijacks on a scale that had never been seen before. The past few years have seen no shortage of other documented BGP hacks that have occurred in the wild.To prevent future incidents, ISPs and backbones will have to be more stringent than they currently are about trusting newly announced routes.
"This hijack highlights a common problem that arises due to lack of route filtering," Alexander Lyamin, CEO of Qrator Labs, told Ars. "We can blame AS39523 for the accident. But without proper filters at the intermediate transit providers' boundaries, we are doomed to see similar incidents again and again."
reader comments
104