What it's like to live under the Google Advanced Protection Program

I am not what I'd call a Very Important Person. I still consider myself a journalist of sorts (and it's what's on my college degree), but I wouldn't say I practice it in the way I did back when I made newspapers. I also am neither an activist, business leader, or am on a political campaign team.
Am I really a candidate for Google's Advanced Protection Program? Do I really need the strongest account security Google offers publicly?
I'll answer that in a minute. But first, I'll define what I think I am these days: I'm approaching middle age while watching my daughters begin their online lives, and I'm as convinced as ever that the Internet is inherently backwards and broken, and we all need to take our online security more seriously. (That is, if we're thinking about it at all.)
The question you have to ask yourself is why wouldn't you want to protect your online life as best you can.
Two-factor security should be mandatory. If a service doesn't provide it, you probably shouldn't use that service. But all two-factor schemes are not created equal. One-time passwords sent by SMS can be intercepted by a determined attacker. Software-based tokens are better, but not infallible. Better, still, are physical hardware keys. A physical key that you plug into a computer via USB, or by NFC or Bluetooth, that you connect to an account. Don't have the key? You're not getting in.
This is all part of the FIDO Alliance — "the World's Largest Ecosystem for Standards-Based, Interoperable Authentication" — and U2F, the "Universal 2-Factor" experience born from FIDO. You can basically think of U2F and 2FA as the same thing, and FIDO is the group that makes the standard happen, with folks from Google, Microsoft, Lenovo and Amazon (among others) on its board.
Subscribe to Modern Dad on YouTube!
The basics of the Advanced Protection Program
Physical hardware keys have been around as a second form of authentication for years, and they've been an security option for Google accounts for quite some time.
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android
Google's Advanced Protection Program makes them a mandatory mechanism for logging in, and it makes them the only 2FA option. You'll still have your Google password, and now you'll have to use a physical hardware key in conjunction with that password to access your account. No more SMS codes. No more Google Authenticator app. No phone calls. It's password-and-key, or you're not getting in.
It's that simple, really. But Google does go a bit further. You'll still be able to log in to websites with your Google account. But apps that can access Gmail or Google Drive files will be severely limited. Here's how Google puts it:
To help protect you, Advanced Protection allows only Google apps and select third-party apps to access your emails and Drive files.As a trade-off for this tightened security, the functionality of some of your apps may be affected. Most third-party apps that require access to your Gmail or Drive data, such as travel tracking apps, will no longer have permission. And you will only be able to use Chrome and Firefox to access your signed-in Google services like Gmail or Photos.Apple's Mail, Calendar, and Contacts apps will continue to be able to access your Google data as normal.
That'll probably be the biggest hurdle you'll face in day-to-day use.
Google also throws extra roadblocks in front of someone if they try to pretend that they're you and you're logged out of your account.
A common way that hackers try to access your account is by impersonating you and pretending they have been locked out of your account. To give you the strongest protection against this type of fraudulent account access, Advanced Protection adds extra steps to verify your identity during the account recovery process.If you ever lose access to your account and both of your Security Keys, these added verification requirements will take a few days to restore access to your account.
That's not one I've had to experience yet, but it doesn't sound like fun.
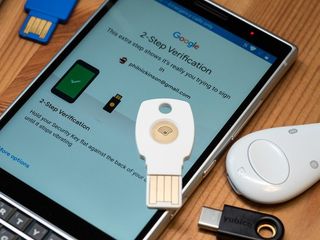
What it's like to use Google Advanced Protection Program
First, hit up Google's Advanced Protection Program website. You'll be instructed to grab a couple of U2F keys. Previously Google recommended third-party keys, which are fine. But now that the Titan keys are available in the Google Store, it's just as easy to grab them. The way you use them will be exactly the same.
Once you have them, you'll actually enroll in the service. That'll turn on all the protections — and it'll also log you out of everything, for obvious reasons.
So, it's time to log back in. Or not. This is where things get a little interesting.
I now have to use Gmail in a web browser instead of in a wrapper like Mailplane or Shift. That's been a minor annoyance, but not really a showstopper. (Hell, it's one fewer app to be running in the background.) But it also means that Mac OS no longer has access to Gmail, either. That actually was a little surprising, given how well the Advanced Protection Program works with iOS via a helper "Smart Lock" app. Maybe it'll change at some point. But on the other hand I wouldn't trade Gmail in a browser for Apple's Mail app.
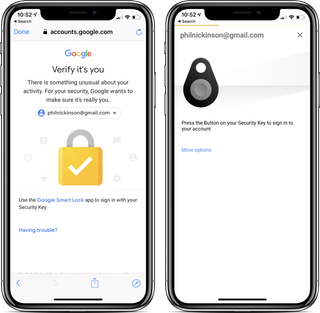
Logging back into phones was easy enough. For that I used my Bluetooth/USB fob. The one I've had for a month or so now charges via microUSB, which is a little annoying. But, again, not a deal-breaker. If I want to use it with a phone, I connect via Bluetooth. If I want to use it with a computer, I plug it in. Easy enough. I've also used the Yubikey Neo, which is USB-A and has NFC built in, and it works great, too. Note that if you're using an iPhone, you'll need something with Bluetooth, at least until NFC is officially opened up in iOS 12.
Logging into a Pixelbook took all of 10 seconds. Type in my password, plug in a key and authenticate, and I'm up and running. (Though if you're really using a Chromebook and really using Advanced Protection you'll want to make sure you have other basic log-in security implemented, so someone can't just open the thing up and start using it. Same as any other laptop, really.)
The biggest hiccup for me has been with the NVIDIA Shield TV. (When you get logged out of everything, you get logged out of everything.) You'd think you'd be able to log into just like an Android phone. (Because it's an Android platform, after all.) But for whatever reason, it just doesn't work, same as if you tried to log in with some other untrusted third-party source.
Beyond that, things pretty much have been seamless. It's not like I have to log in to my account every day. (Though in some business environments, that's exactly what this physical key scheme is great for.)
If I do need to log in to a new device somewhere, I just have to make sure I have my key on me. So I keep one on my keys, and a backup in a safe place. (No, I'm not telling you where.)
By the way: You can un-enroll from the Google Advanced Protection Program if you just can't live with it. But I haven't felt that urge at all. Also, you can un-enroll keys from any service at any time -- you'll just have to remember which services you use a key with. (Or you can always just destroy a key if you're done with it.)

Which U2F key is best for Advanced Protection?
Here's where things really come down to your own situation. You can get a straight USB-A key. You can get a USB-C key. You can get a nano key (USB-A or USB-C) that lives in your laptop most of the time but doesn't get in the way (outside of taking up a port). You can get something with Bluetooth, or NFC.
You don't have to use Google's Titan Security Key if something else will work better for you.
(A note on that, though: The USB model of Google's Titan Security Key includes NFC, but it won't work at launch. That'll require a behind-the-scenes update on your phone. Other hardware keys handle NFC just fine, though, if you have to have it right this second.)
It all depends on just how often you need to log in to whatever it is you need to log in to, and the kind of device you're using. If your business requires daily authorization, but at a trusted computer (say, behind a bunch of locked doors), then maybe a USB-A nano key is the way to go. If, like me, you don't need to log in very often but still want everything Advanced Protection offers, something larger might not be awful. If you have a USB-C laptop and USB-C phone, well, that makes that decision even easier. It's going to vary depending on what you use.
And you don't necessarily need Google's Titan key, either. They function exactly the same as other U2F keys — only these have the might of Google behind them, controlling the firmware that's inside. (And that is a good selling point.) And unlike other keys, which can be manipulated by an IT department, the firmware is totally locked down. You'll be using these as Google intended.
So is Google's Advanced Protection Program the right thing for you?
That's one of those things that I can't answer for you.
The Advanced Protection Program is a little overkill, but it's also the right way to do security.
On one hand, I want to say yes, it is. I've found the tradeoff between security and annoyance to be minimal. It's not going to completely replace SMS codes and software-based tokens in any event, though it'd be nice if it did. The simple fact is not enough services use hardware keys. (And some only allow them as secondary 2FA methods.) Hit up twofactorauth.org to find out if your favorite service uses them.
And I'm really close to putting my daughter's account on it. (If I haven't already, because now that I'm writing this …)
I've had to help too many family members reclaim accounts before. It's just too easy to accidentally click on links that should never have been clicked. It happens to the best of us.
What we need is stronger back-end support to go along with the knowledge that the internet is backwards and broken and we have to be more vigilant.
Google Advanced Protection gives that support.
It's just up to us to use it. And I'm not turning it off.

