Remote macOS exploit using custom URL schemes demonstrated by security researcher
Researchers demoed a recently discovered exploit in macOS that allows malware to be remotely installed on a target machine through the use of custom URL handlers in Safari.
The WINDSHIFT APT deals largely with "Do you want to allow" popups familiar to any macOS user, explains security researcher Patrick Wardle. These document handlers are frequently seen in use when clicking on an App Store link or PDF, which asks users for permission before opening the link or file in a registered app like the Mac App Store or Preview.
Custom URL handlers, and similarly document handlers, are basically a way for an application to notify the OS they are able to handle certain document types. For example, VLC advertises the ability to accept many different video formats, while Preview does the same for a wide array of different file types.
It is through these handlers that the exploit exists.
Wardle gives an excellent in-depth explanation that many developers will appreciate, but the basic method for this exploit is as follows.
Exploit process
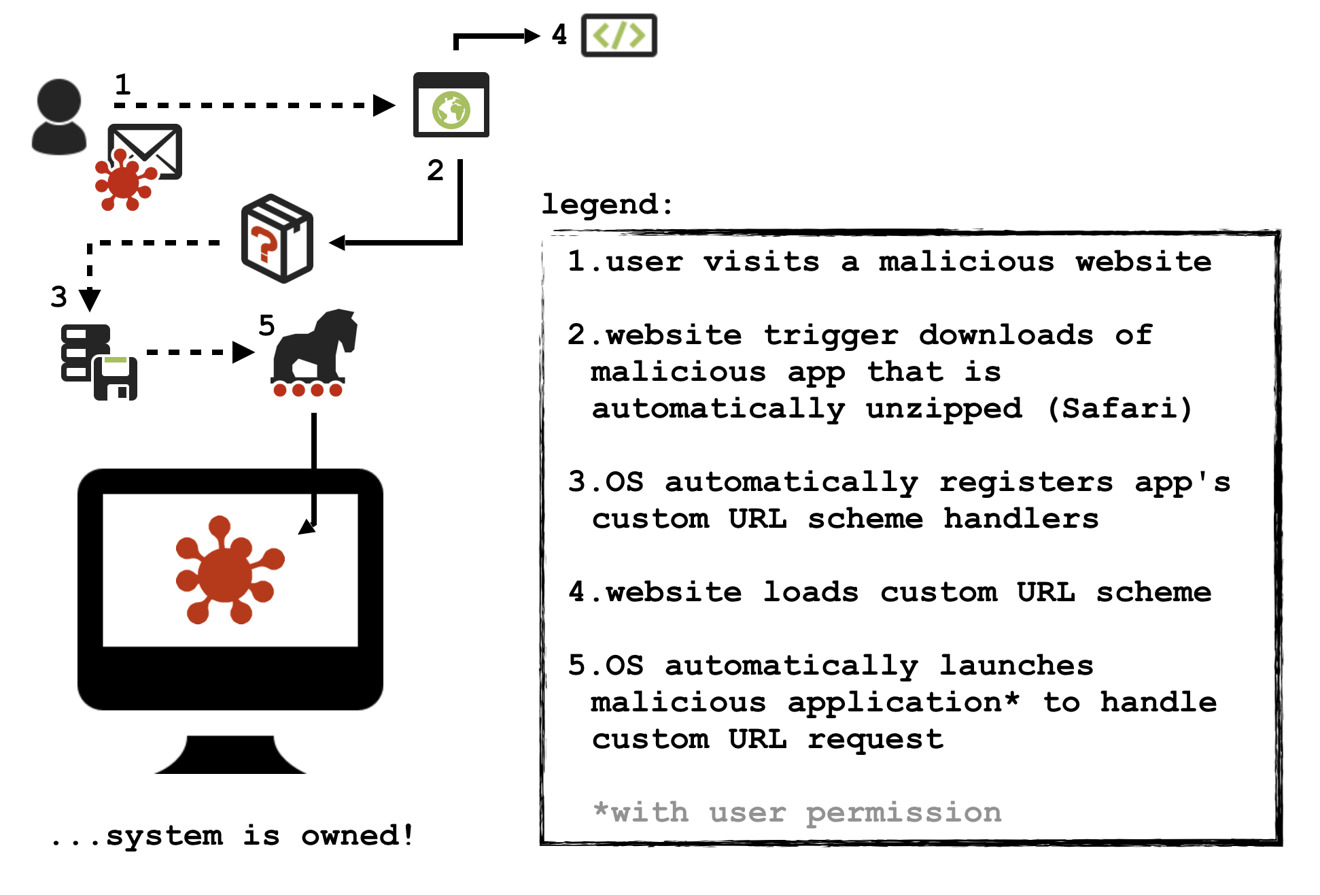
First, the malware is uploaded to a malicious website. When visited, the malicious .zip file is downloaded by macOS, which automatically unzips it. Apple allows the unzipping of files it deems "safe," which includes this piece of malware if a user downloads it via Safari.
Once the file is unzipped, the malware application is able to register its custom URL scheme handler with the file system. Code in the malicious webpage can then load or "browse" to the custom URL, Wardle says, triggering macOS to look up the just installed URL handler and launch the malicious app.
While Safari does prompt the user to Cancel or Allow the operation to run, developers are able to change the application text to something designed to be misleading. Instead of saying "Do you want to allow Safari to open scary malware application?" it could say "Do you want to allow Safari to open Preview?"
Then the OS attempts to launch the malware that is sitting in your downloads folder.
Prevention
Several preventative measures are built into macOS, though they aren't necessarily effective in this instance. The first barrier is requiring the user to click Allow on the popup in Safari, but the custom text makes it easy to craft a seemingly mundane and trustworthy message.
The same goes for File Quarantine. The safety mechanism will ask the user for confirmation before installing the software, but here, too, the name can be changed.
GateKeeper is also most likely bypassed as explained by Wardle.
"In its default configuration, Gatekeeper allows signed applications," he writes. "The malware used by the WINDSHIFT APT group was signed (as is most Mac malware these days). So Gatekeeper doesn't even come into play!"
Apple can revoke an app's signature once it is discovered to be used for malware, but that doesn't help for those who were already tricked into running the application.
Users who are most worried about this exploit have an easy solution if they'd like to play it safe: just turn off automatic unzipping of safe files.
In Preferences, navigate to Safari > General, then uncheck Open "safe" files after downloading.
Technically, macOS is doing everything correctly, but it is a series of innocuous actions that can allow a piece of malware to be installed unbeknownst to the user. Apple could elect to make some changes to the process in future updates, such as automatically preventing files from unzipping by default.
 Andrew O'Hara
Andrew O'Hara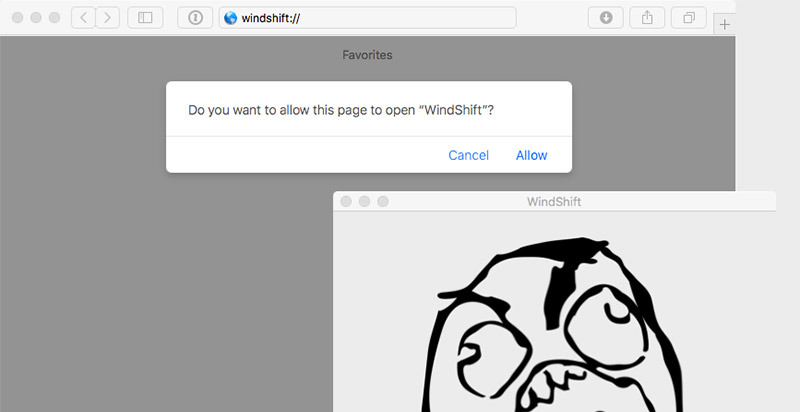










 Amber Neely
Amber Neely
 William Gallagher
William Gallagher

 Malcolm Owen
Malcolm Owen