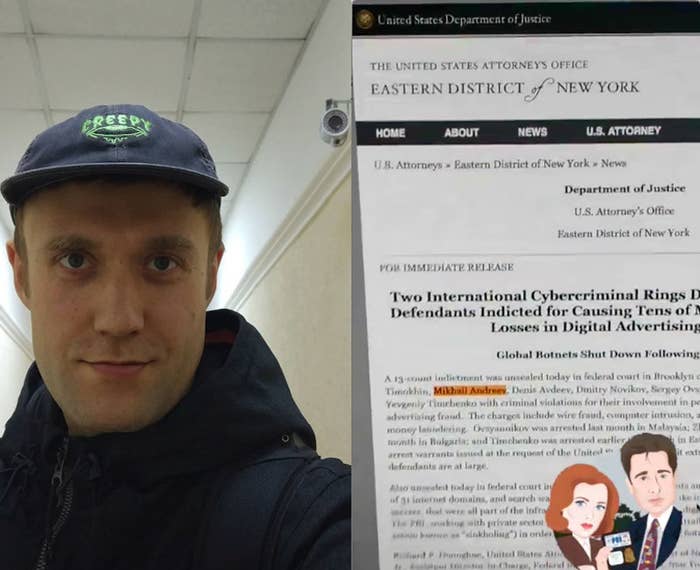
When he was arrested in Malaysia last month, Sergey Ovsyannikov was told by US law enforcement that he had the right to remain silent. Instead, the 30-year-old native of Kazakhstan quickly admitted to helping run a massive ad fraud operation that allegedly stole tens of millions of dollars.
Ovsyannikov’s confession is contained in a trove of unsealed court documents that provide new insight into the FBI’s biggest-ever ad fraud investigation. Last week, the Department of Justice announced a 13-count indictment against Ovsyannikov and seven other men for allegedly operating two lucrative ad fraud schemes that utilized bots, thousands of counterfeit websites, and roughly 1.7 million infected PCs to pillage the global advertising industry.
Billions are stolen each year by people like Ovsyannikov who exploit the systems used to buy and sell digital advertising. In this case, they allegedly programmed bots to generate fake web visits to websites they had created, thereby earning revenue from the real ads that appeared on these sites. The accused are also alleged to have sold their fake traffic to other customers.
Ovsyannikov and two others are accused of running a scheme called 3ve (pronounced “eve”). BuzzFeed News previously revealed how an unprecedented industry coalition of more than 15 technology companies, including Google and White Ops, investigated and helped take 3ve down. The five other men facing charges allegedly operated Methbot, a different scheme that was revealed publicly in 2016 by White Ops.
“As alleged in court filings, the defendants in this case used sophisticated computer programming and infrastructure around the world to exploit the digital advertising industry through fraud,” Richard P. Donoghue, United States attorney for the Eastern District of New York, said in a press release announcing the indictment.
A law enforcement source told BuzzFeed News that the investigation is ongoing. Future charges could relate to 3ve, as it involved three unique traffic-fabrication operations, though only one was cited in the indictment.
Along with Ovsyannikov, two other men are in custody and awaiting extradition to the US: Aleksandr Zhukov, who was arrested in Bulgaria in early November, and Yevgeniy Timchenko, who was recently arrested in Estonia. Timchenko and Ovsyannikov allegedly worked together to operate 3ve. Zhukov was named as the CEO of the Methbot operation in the indictment. Five other men, all Russian, remain at large.
Yermek Rakhmetov is a friend of Ovsyannikov’s and the CEO of Ping Media, a digital advertising company in Kazakhstan. When reached by BuzzFeed News, he was surprised to learn Ovsyannikov had been arrested and found it hard to believe he’d done something illegal.
“I know him like a friend, we worked together,” he said in English, his second language. “I know that he is a very clever guy who knows about internet advertising. I work in this field also, but I didn’t assume that he could do some fraud ads.”
Rakhmetov said he last spoke to Ovsyannikov on Oct. 4, when he sent his friend a birthday message. “He replied to me and said everything is OK,” Rakhmetov said. Less than three weeks later, Ovsyannikov was taken into custody.
Others named in the indictment are unlikely to see a US courtroom. One of them is Mikhail Andreev, 34, who allegedly worked as a programmer on Methbot. He’s a Russian citizen currently living in Crimea, which was annexed by Russia in 2014. The US and Russia do not have an extradition treaty.
“I’m not guilty, I don’t have much more to say really,” Andreev said in a message sent in Russian to BuzzFeed News on the Telegram messaging app.
Andreev initially agreed to an interview, but quickly canceled, telling a reporter that he’s “very busy.” (Almost two weeks after this story went online, he published a blog post to declare his innocence and say that he has asked the FBI to "remove my name from the list of suspects, since I have never taken any illegal actions.")
Andreev was clearly thinking about his legal situation in the wake of the indictment. After news of the charges first broke, he shared an image of the court filing on his Instagram with the comment, “I wonder what will happen next...”
In another Instagram post, he commented on the fact that the indictment included communications between him and his alleged conspirators. “Big Brother is in action: private search and texts,” he said.

Andreev, who goes by the online nickname adw0rd, has a presence on many social media platforms. Typically, he shares photos and videos of him skateboarding. In one Instagram post, he brags that the Kremlin propaganda channel Russia 1 had profiled him for a TV story.
There’s also evidence that Andreev and fellow accused Boris Timokhin have known each other for years. Andreev mentions his alleged conspirator in a 2012 blog post about building a piece of software. (Messages sent to social media accounts and email addresses belonging to others named in the indictment went unanswered.)
The private messages, search history, and other information that drew Andreev’s ire on Instagram were obtained by the FBI thanks to warrants issued by New York federal judges. The warrant applications relied on detailed affidavits submitted by FBI agents and NYPD officers, and these affidavits are contained in recently unsealed court documents.
They describe how the alleged fraudsters ran their operations and the ease with which they allegedly stole tens of millions of dollars. The court filings also underscore how these schemes were in many ways run like small technology startups.
The alleged operators set up front ad tech companies with websites and also appear to have used common tools such as Trello project management software and Google apps to manage their operations and communicate. They created spreadsheets to keep track of the servers they rented, and Ovsyannikov allegedly used Trello to collaborate with others involved in 3ve.
One court filing describes him creating a Trello card that listed hundreds of domains of real websites they were planning to impersonate as part of the scheme. The use of collaboration software also helped the FBI identify who Ovsyannikov was working with, according to the documents.
After obtaining a warrant to search his email, FBI agents saw that Ovsyannikov had added two other people, Yevgeniy Timchenko and Aleksandr Isaev, to a shared spreadsheet that mapped out the technical infrastructure of 3ve. “Specifically, Timchenko had editing privileges and Isaev had reading privileges,” wrote FBI Special Agent Evelina Aslanyan in an affidavit in support of arrest warrants for the three men.
After being arrested, Ovsyannikov told US law enforcement that he and his two partners operated companies called Adzos and Clicklandia, according to court documents. These front companies helped them secure agreements with legitimate players in the ad ecosystem.
Ovsyannikov admitted that “approximately 97% to 98% of Adzos’ business revenues were not legitimate,” according to an affidavit from NYPD Detective Mark Rubins, a member of the FBI Financial Cyber Crimes Task Force.
The Adzos website now carries a notice that it’s been seized by the FBI, but earlier versions of the site are available from the Internet Archive. The company promised advertisers that its “array of modern monetization approaches guarantees the success of your advertising campaign.” In reality, the traffic was generated thanks to PCs infected with malware that secretly loaded webpages with ads. (See this previous story for a detailed description of how the malware generated fake traffic.)
The Department of Justice alleges that 3ve made use of roughly 1.7 million infected PCs. In order to document the presence of malware on computers in New York, and to identify how it worked, FBI agents visited the homes of more than a dozen US citizens and businesses in the New York area. They informed people that their PC was infected and requested permission to access the machine. Agents then monitored the computers to identify the servers they communicated with, which revealed the command and control operation at the heart of the malware.
This malware helped Ovsyannikov and his alleged collaborators generate millions of dollars in revenue, according to court documents.
One affidavit from Rubins said a bank account in the Czech Republic connected to the 3ve operation received $11.6 million in payments from legitimate advertising companies over a 12-month period. During its existence, that account received a total of $17.6 million in transfers. It was one of several accounts operated by the fraudsters, according to court filings.
Money was on Ovsyannikov’s mind when he was arrested in Malaysia on Oct. 23. After admitting to his involvement in 3ve, Ovsyannikov said he and Isaev had created a company called Octmedia LP to be the main recipient of their advertising revenue. The FBI later obtained a contract between Ovsyannikov and Isaev that stated the former would be paid a salary of $10,000 a month by Octmedia “for technical support services.”
Once in custody, Ovsyannikov said he wanted to make sure the money continued to flow. “He further stated that after his arrest he had asked his wife to speak to an accountant to ensure that his salary payments continue to be received,” wrote Rubins.
Roughly two weeks later, US law enforcement used that information to seize bank accounts belonging to Octmedia and another company controlled by Ovsyannikov.
UPDATE
A comment from Andreev's blog post was added to the story.

