
Phishers are deploying what appears to be a clever new trick to snag people’s Facebook passwords by presenting convincing replicas of single sign-on login windows on malicious sites, researchers said this week.
Single sign-on, or SSO, is a feature that allows people to use their accounts on other sites—typically Facebook, Google, LinkedIn, or Twitter—to log in to third-party websites. SSO is designed to make things easier for both end users and websites. Rather than having to create and remember a password for hundreds or even thousands of third-party sites, people can log in using the credentials for a single site. Websites that don’t want to bother creating and securing password-based authentication systems need only access an easy-to-use programming interface. Security and cryptographic mechanisms under the hood allow the login to happen without the third-party site ever seeing the username and password.
Researchers with password manager service Myki recently found a site that purported to offer SSO from Facebook. As the video below shows, the login window looked almost identical to the real Facebook SSO. This one, however, didn’t run on the Facebook API and didn’t interface with the social network in any way. Instead, it phished the username and password.
Just add HTML
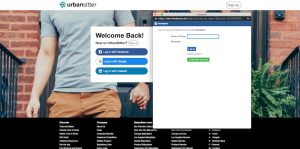
While the replica is convincing, there was one easy way any user could immediately tell it was a fake. Genuine SSOs from Facebook and Google can be dragged outside of the window of the third-party site without any part of the login prompt disappearing. Portions of the fake SSO, by contrast, disappeared when doing this. Another tell-tale sign for Myki users, and likely users of other password managers, was that the autofill feature of the password manager didn’t work, since contrary to the address showing in the HTML block, the actual URL the users were visiting wasn’t from Facebook. More advanced users almost certainly could have spotted the forgery by viewing the source code of the site they were visiting, too.
The convincing forgery is yet another reminder that attacks only get better. It also reaffirms the value of using multi-factor authentication on any site that offers it. A password phished from a Facebook account that used MFA protection would have been of little use to attackers since they wouldn’t have had the physical key or smartphone that’s required when logging in from a computer that has never accessed the account before. Facebook has more tips for dealing with phishing here.
reader comments
70