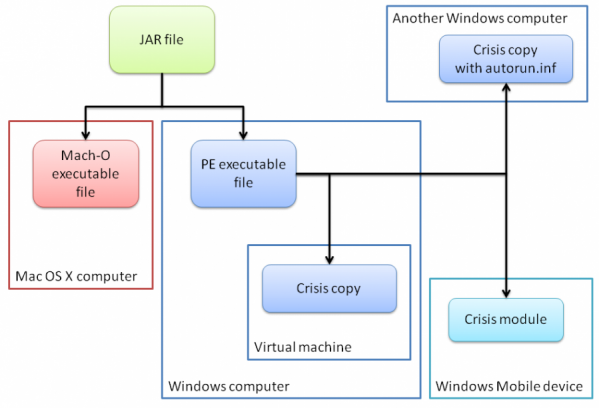
Researchers have uncovered a single espionage malware attack that is capable of infecting multiple platforms, including computers running the Windows and Mac OS X operating systems, Windows-powered mobile devices, and VMware virtual machines.
When Ars first chronicled the trojan backdoor known as Morcut last month, we reported that it turned Macs into remote spying devices that were capable of intercepting e-mail and instant-message communications and using internal microphones and cameras to spy on people in the vicinity of the machine. Since then, researchers have developed a more comprehensive view of the malware, which is known by the name "Crisis." A JAR, or Java archive, file that masquerades as a legitimate Adobe Flash installer allows attacks to infect a much wider variety of platforms, including virtual machines, which many people use to protect themselves from infection when performing online banking or while researching malicious websites.
"This may be the first malware that attempts to spread onto a virtual machine," Takashi Katsuki, a researcher with antivirus provider Symantec, wrote in a blog post published on Monday. "Many threats will terminate themselves when they find a virtual machine monitoring application, such as VMware, to avoid being analyzed, so this may be the next leap forward for malware authors."
When encountering a Windows-based PC, Crisis actively searches for VMware virtual machine images. When they're found, the malware copies itself onto an image using VMware Player, a tool that makes it easy to run multiple operating systems at the same time on the host machine.
"It does not use a vulnerability in the VMware software itself," Katsuki wrote. "It takes advantage of an attribute of all virtualization software: namely that the virtual machine is simply a file or series of files on the disk of the host machine. These files can usually be directly manipulated or mounted, even when the virtual machines is not running."
As illustrated in the image above, the JAR file first determines whether it's present in a Mac or Windows environment. When loaded onto an OS X machine, Crisis accesses a Mach-O file that's capable of running on Macs. When loaded into a Windows environment, the malware uses a standard Windows executable file to infect PCs, the VMware Player attack to infiltrate virtual machines, and a module that targets Windows Mobile devices when they're connected to a compromised Windows computer.
So far, Crisis has been detected on fewer than 50 machines worldwide, according to data from Symantec. But given its ability to infect Macs and Windows PCs with a backdoor that taps communications sent by Skype, Adium, MSN Messenger and other apps, Crisis was already considered to be important. It's even more noteworthy now that its virtual-machine capabilities have been uncovered.
reader comments
31