New Mac Spyware Discovered – OSX/Dockster.A
Posted on
by
Lysa Myers
Update: December 3, 2012
This malware is now known to be in the wild, on a website dedicated to the Dalai Lama, and the remote address contacted by the backdoor is now active. The exploit code used to drop the backdoor is the same as that used by SabPab. This is still considered to be low-risk as this is not known to be widespread and the vulnerability targeted by the exploit code is corrected by the latest version of Java.
A sample of a new Mac spyware called OSX/Dockster.A was found today on VirusTotal. This trojan is currently considered low risk as it is not known to have infected users. It has backdoor functionality, including a keylogger component that records an affected user’s typing.
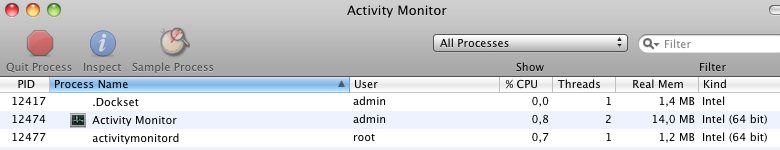
If it’s executed, the trojan deletes itself from the location where it was run and installs itself in the user’s home directory with the filename .Dockset. The file is not visible through Finder; however, if it’s running, it can be seen within OS X’s Activity Monitor. It creates a launch agent called mac.Dockset.deman so that the trojan will restart each time an affected user logs in. Once the trojan is active, it tries to contact the remote address itsec.eicp.net to await instructions. At the time of writing, this address is not registered, which indicates the sample may be intended simply as a test rather than an active threat.
The backdoor functionality of this trojan is quite basic – it provides a simple remote shell which allows the trojan’s controller remote access, it allows the controller to download additional files, and it logs keystrokes.
Intego VirusBarrier users with up-to-date virus definitions are protected from this threat, which is detected as OSX/Dockster.A.