
For the second time in a month, Apple has effectively blacklisted the current version of the Java Web plugin on OS X. The block comes just days after it was discovered that the latest version of the plugin, which had been rushed out to patch a critical vulnerability, can still be exploited despite its heightened security mechanisms.
Apple has worked to distance itself from Java in recent years. The company deprecated its own version of the Java virtual machine for OS X, instead deferring development to Oracle itself. The browser plugin in particular has become a common vector for malware attacks, and Apple removed the Java Web plugin from recent versions of OS X last year. Those needing the plugin must install it separately.
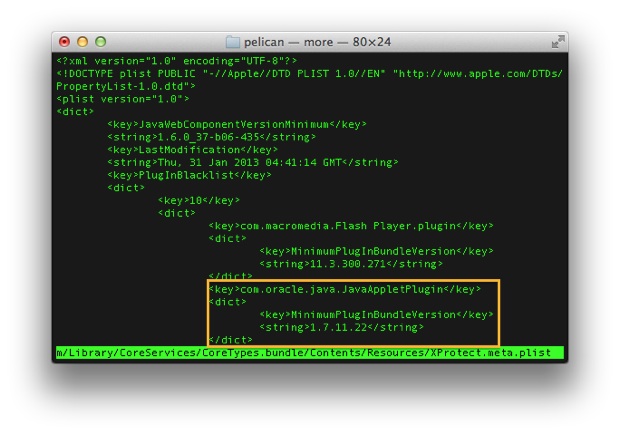
Apple has also added additional security controls to OS X, including a mechanism that forces its Safari browser to use a minimum specified version of various plugins, such as Flash or Java. When security vulnerabilities are discovered in various plugins, Apple can update its Xprotect list to specify which version is acceptable. Earlier versions of plugins are then blocked from running within Safari.
Apple has used the Xprotect minimum version mechanism to effectively block the Java Web plugin by specifying a future version number that hasn't been released. It used this technique earlier this month when a particularly "critical" exploit in the plugin was discovered by security researchers and was determined to be "massively exploited in the wild."
Oracle worked to quickly fix the bug, and it released a new version (JRE version 1.7.0_11-b21) of the Java plugin a few days later. Apparently the fix wasn't complete—one part of the vulnerability still existed—but Oracle also set the plugin's default security setting to "high," which required users to actively click "OK" to run any unsigned or self-signed Java applets. Java applets signed by trusted authorities would still run without user intervention.
Unfortunately, the security mechanism itself turned out to be vulnerable due to additional bugs discovered in the Java frameworks. Security researchers revealed on Sunday that the bug could allow unsigned applets to run inside a browser without prompting a user to allow its execution.
It appears that Apple has once again decided to block the Java plugin from running on OS X by requiring an as-yet unreleased version (JRE version 1.7.0_11-b22) in Xprotect, according to MacGeneration. Users who rely on Java applets for specific functions, such as banking, will have to try alternate browsers such as Chrome or Firefox.
Such alternatives might not be available for long, however. Chrome is increasingly blocking plugins with known security vulnerabilities. On Tuesday, Mozilla announced that it will soon block Java in Firefox. While Firefox already uses a mechanism similar to Xprotect, which requires minimum approved versions of plugins and uses "click to play" by default, a future version will block all content that requires Java, Adobe Reader, or Microsoft Silverlight to play. Users who want content based on those software frameworks will have to explicitly approve it by clicking on an icon.
reader comments
60