
Researchers have found a shortcoming in key security protection recently introduced in the browser plugin for Oracle's Java software framework, a flaw that makes it easier for attackers to sneak malware onto end-user computers.
By default, the widely used plugin doesn't check the status of digital certificates used to sign Java apps hosted on websites, Ars Technica has confirmed. As a result, Java presents certificates as trustworthy even when they've been reported as stolen and added to publicly available revocation databases. The failure of Java to check certificate revocation lists came to light on Tuesday when a legitimate site was found hosting a malicious app. Java presented an accompanying certificate as a trusted credential belonging to Texas-based Clearesult Consulting Inc. even though the firm had issuer GoDaddy revoke the certificate in December.
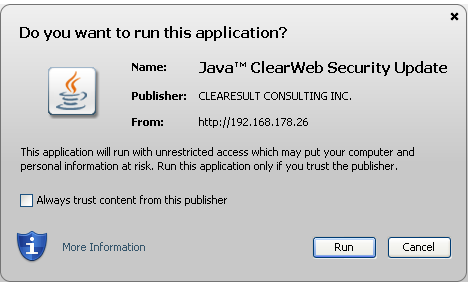
"Java thinks the stolen certificate used is 100% valid and should be trusted," Jindrich Kubec, director of threat intelligence at antivirus provider Avast, wrote in an e-mail. Referring to certificate revocation lists and an alternate method for invalidating credentials known as the online certificate status protocol, he added: "With CRL/OCSP it would make it untrusted and probably present completely different dialogues or even won't allow running the applet at all—unfortunately, the situation is a bit complicated with testing this behaviour, so I can't tell for sure which of the above would be true."
The failure to vet the status of certificates dilutes a key security protection Oracle recently added to Java. Starting in January, the default security configuration was set to "high," causing a browser to seek user permission before running unsigned apps. Since Java treats apps signed by a compromised certificate as trusted, there's the possibility that end users will receive no such prompt, a shortcoming that significantly diminishes the benefit of this important new measure. Even if users are prompted, the dialog informs them the app is trusted without taking the time to see if the underlying certificate is still valid. That omission makes it hard for users to make an informed choice. As Kubec explained, the precise behavior is hard to determine. Certificate thefts have long been a favorite tactic for sneaking malware past computer security checkpoints.
An Oracle blog post documenting the Java security settings doesn't clarify, and Oracle representatives didn't respond to an e-mail seeking comment for this post. Sadly, an e-mail sent to 13 valid addresses inside the company's PR department didn't even receive an acknowledgement that the request had been received.
Oracle should be commended for the change it introduced in January, which caused browser plugins—at least in some cases—to prompt users before running Java apps. Moves that limit functionality or require end users to click through prompts are usually extremely difficult to implement because marketers want their software to be as easy as possible to use. Requiring prompts where they previously hadn't been required was a courageous step and the right thing to do, given the steady stream of Java-based attacks found online over the past year that surreptitiously install highly malicious software on computers.
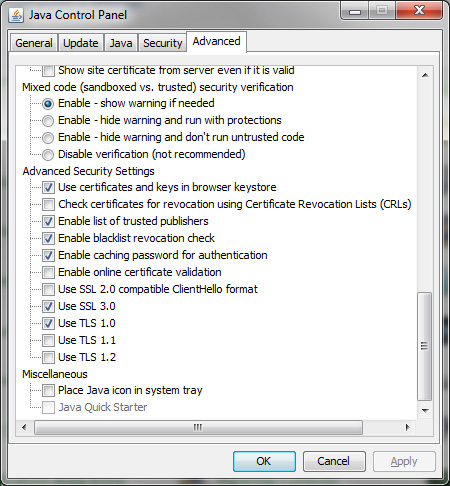
But the move is clearly not enough. The malicious Java app discovered earlier this week was hosted on a legitimate German dictionary website that was most likely compromised by the same party that planted the attack. Given this real-world threat, Ars once again advises readers who don't regularly use Java to consider uninstalling it altogether, uninstalling just the Java browser plugin, or using a dedicated browser to access the handful of sites they frequent that require Java and using a different, non-Java-enabled browser for general surfing. At the very least, those running Java should access the program's advanced settings and check the box next to "Check certificates for revocation using Certificate Revocation Lists (CRLs) and set Java's security level to "very high" under the general security tab.
reader comments
105