Overlooked in last week's revelation that the National Security Agency (NSA) is harvesting hundreds of millions of e-mail address books around the world was this surprising factoid: Apple makes this mass collection easier because the Address Book app that by default manages Mac contacts doesn't use HTTPS encryption when syncing with Gmail accounts.
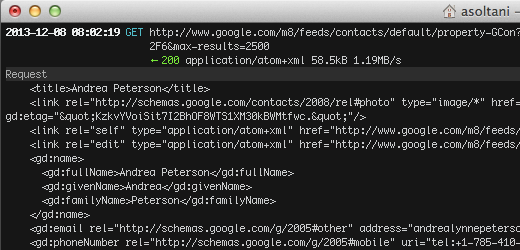
As a result, addresses that automatically travel between Macs and Google servers are sent as plain text, independent privacy researcher Ashkan Soltani wrote in The Washington Post last Monday. He provided the above screenshot demonstrating that Address Book contents appear in the clear to anyone who has the ability to monitor traffic over a Wi-Fi network or other connection. His observation came 15 months after another Mac user also warned that the Mac app offered no way to enable HTTPS when syncing e-mail address lists with Gmail.
"It appears that it's an Apple issue," Soltani told Ars, referring to the inability to enable HTTPS when Apple's Address Book is updated to a user's Gmail account. "Their other products support Gmail via HTTPS, so I suspect it would be a three-line fix in the contacts to alleviate this problem."
In fairness to Apple, Soltani pointed to this description of the Google contacts programming interface, which was officially discontinued in April 2012. It indicated HTTP as the sync mechanism for address books. It's possible Apple developers haven't updated their code since Google introduced the change. It's also possible the lack of HTTPS encryption will be fixed in Mavericks, the upcoming version of Mac OS X that Apple is expected to unveil Tuesday.
Once the current version of Address Book is configured to sync with Google's popular e-mail service, the Apple app checked in about once an hour on Macs Soltani tested. Any time the app contained an address not found in Gmail, it would send the data unencrypted. Interestingly, the program uses the HTTPS protocol to cryptographically authenticate the machine advertising itself as a Gmail server, but the app goes on to send the addresses in plain text over an unencrypted HTTP connection, he said.
According to The Washington Post, the NSA’s Special Source Operations branch collected 444,743 e-mail address books from Yahoo, 105,068 from Hotmail, 82,857 from Facebook, and 33,697 from Gmail during a single day last year. The comparatively low number of contact lists acquired from Gmail is noteworthy considering it is among the most widely used online e-mail services. A key contributor to that low rate is almost certainly Google's default use of HTTPS to encrypt e-mail traffic. Soltani said the protection is not available unless applications that connect to Gmail support encryption. The application programming interface (API) that makes that capability possible is missing from Apple's address book, he added.
"There's still a lot of areas where developers just rely on insecure APIs, and this data shows that," he told Ars. Soltani said he found no evidence that Thunderbird and other popular apps didn't provide a way to encrypt data when working with Gmail.
Cryptography expert and security analyst Bruce Schneier said in a recent blog post that NSA spies acquire the address lists by tapping the Internet backbone.
"Once they have the data, they have powerful packet inspectors—code names include TUMULT, TURBULENCE, and TURMOIL—that run a bunch of different identification and copying systems," he wrote. "One of them, code name unknown, searches for these contact lists and copies them. Google, Yahoo, Microsoft, etc., have no idea that this is happening, nor have they consented to their data being harvested in this way."
Apple representatives didn't respond to an e-mail seeking comment for this post.

reader comments
67