Researchers have identified new self-replicating malware that infects computers running the Apache Tomcat Web server with a backdoor that can be used to attack other machines.
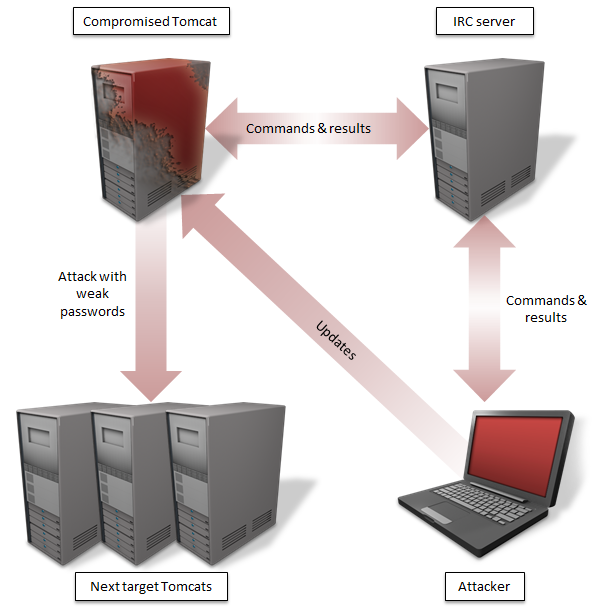
Java.Tomdep, as the backdoor worm has been dubbed, is Java Servlet-based code that gives Apache Tomcat platforms malicious capabilities. It causes infected machines to maintain Internet relay chat (IRC) communications with attacker servers located in Taiwan and Luxembourg. The control servers send commands and receive progress reports to and from the infected machines. Affected platforms include Linux, Mac OS X, Solaris, and most supported versions of Windows. Researchers haven't said precisely how the malware takes initial hold of servers, but there's no evidence yet it exploits any vulnerability in Tomcat or any other software running on infected servers.
In a blog post published Wednesday, Takashi Katsuki, a researcher at security firm Symantec, said Java.Tomdep appears to be designed to harness the huge amounts of bandwidth and computing power available to Web servers for use in denial-of-service attacks against other machines. Unlike Darkleech and other malware targeting Web servers, there's no indication that it's used to attack end users visiting websites. Katsuki explained:
The Java Servlet is executed on Apache Tomcat, but it does not create a webpage and instead behaves as an IRC bot. It connects to an IRC server and performs commands sent from the attacker. End users who visit webpages from the compromised Tomcat server are not affected by this threat. Aside from standard commands such as download, upload, creating new process, SOCKS proxy, UDP flooding, and updating itself; compromised computers can also scan for other Tomcat servers and send the malware to them. It is thus possible that DDoS attacks from the compromised servers are the attacker’s purpose.
Tomdep-infected machines also seek out other servers running Apache Tomcat and attempt to log in to them using commonly used combinations of user names and passwords. When the credentials match, Tomdep gets installed on another machine.
So far the number of infected machines appears to be low. Then again, the malware was detected less than a month ago. Given the epidemic of weak password hygiene and the lack of antivirus programs used on many Web servers, the threat could still spread.
Post updated to add last sentence in second paragraph.
Listing image by Thomas Stix
reader comments
19