A London-based security researcher made multiple reports to Apple that the company's iCloud service was vulnerable to brute-force password attacks months before the revelations that celebrities' iCloud backups were mined for intimate photos and videos. The Daily Dot reports that Ibrahim Balic sent descriptions of the vulnerability to Apple in March in addition to filing a report that the system leaked user data that could be used to mount such attacks. Balic attempted to reach out both via e-mail and through the company's Web-based bug reporting system.
In an e-mail dated March 26, Balic told an Apple employee:
I found a new issue regarding on Apple accounts (sic)...By the brute force attack method I can try over 20,000 + times passwords on any accounts. I think account lockout should probably be applied. I'm attaching a screen shot for you. I found the same issue with Google and I have got my response from them.
The Apple employee responded, "It's good to hear from you. Thank you for the information."
Balic also reported the bug through Apple's bug-reporting site on March 26, showing the API requests to the iCloud service via secure HTTP that exploit the "Authorization" parameter in the Web request (sent with a fake iPhone client ID and using Apple's iCloud authentication token format), as shown below.
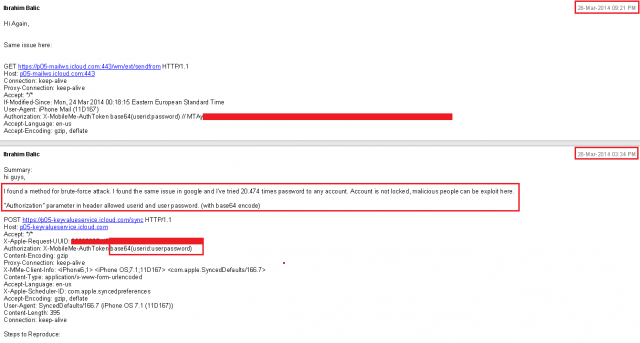
Apple responded in May to Balic, discounting the vulnerability. "Based on the information you provided, it appears that it would take an extraordinarily long time to find a valid authentication token for an account," an Apple product security specialist named Brandon said in an e-mail to Balic. "Do you believe that you have a method for accessing an account in a reasonably short amount of time?"
“I believe the issue was not completely solved," Balic told the Daily Dot. "They kept asking me to show them more stuff."
reader comments
118