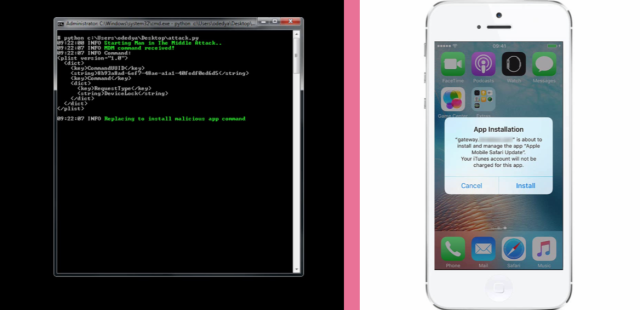
Security researchers at Check Point Software claim to have found a weakness in Apple's mobile device management (MDM) interface for iOS devices that could be exploited to gain complete access to devices. Dubbed "SideStepper," the approach could allow an attacker to hijack enterprise management functions and bypass Apple's application security.
By sending a link to a victim's device, someone could take control of the MDM software on the phone and push potentially malicious applications to the device as well as perform other configuration changes as a remote administrator. While Apple's security screening for the applications it allows into its App Store is rigorous, there is a backdoor left in the screening process: enterprise app stores. And new research by Check Point being presented at Black Hat Asia 2016 shows that even with security improvements in iOS 9, attackers can kick that backdoor in by hijacking the enterprise management connection.
As long as they've registered with Apple's enterprise developer program to get a software signing certificate, attackers can social engineer victims into consenting to install applications that expose nearly every aspect of their phone's settings and data simply by abusing enterprise policy settings.
This sort of abuse of enterprise certificates, as Avi Bashan and Ohad Bobrov of Check Point noted in their paper for Black Hat Asia, is already widespread among third-party app stores for iOS, which register as "enterprises" with Apple and "use the certificates to install apps on their customers' devices, claiming they are 'staff members'." The same approach could be used by developers of malicious applications.
Hacking Team did just this, as was discovered last year when the company's e-mail was hacked—they created a malicious application that was disguised as the iOS Newsstand app, which gave Hacking Team access to the victim's address book, photos, and geolocation data. The app was signed with Hacking Team's own Apple developer certificate, allowing the company to slip past the usual App Store security screening.
Apple made a number of changes in iOS 9 to make this sort of attack more difficult by default, including a more complex verification process for installation. And by default, iOS doesn't allow applications with untrusted certificates to run. However, iOS automatically trusts applications installed through MDM systems, assuming that they have been vetted by the company operating the MDM software. Michael Shaulov, Head of Mobility Product Management at Check Point, told Ars that the MDM interface to iOS 9 is vulnerable to "man-in-the-middle" attacks.
An attacker can send a new profile setting to a targeted victim via SMS that will reroute the phone's data traffic through a malicious proxy—allowing the attacker to monitor for MDM traffic and then respond impersonating the MDM server, using the device-management APIs provided by Apple.
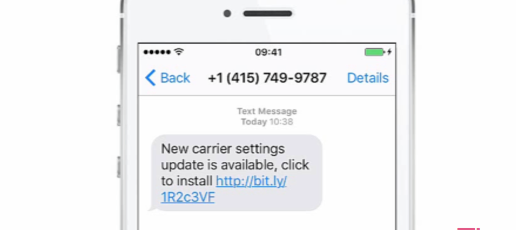
Once they've placed themselves in the middle of the data stream, they can send their own push notifications to install applications to the targeted device, bypassing Apple's extra security and presenting the user with just a single message asking for permission to install.
This sort of attack could conceivably be used on any iOS device enrolled in an MDM system, including personal devices enrolled through an employer's "Bring Your Own Device" (BYOD) program. Once launched, the attacker could use the access to get to any data on the device, its microphone and camera, geolocation information, and other features—as well as gain a foothold within the enterprise itself.
An Apple spokesperson downplayed the vulnerability, however, insisting that it was a social-engineering attack and not a weakness of iOS. “This is a clear example of a phishing attack that attempts to trick the user installing a configuration profile and then installing an app," the spokesperson told Ars. "This is not an iOS vulnerability. We've built safeguards into iOS to help warn users of potentially harmful content like this. We also encourage our customers to download from only a trusted source like the App Store and to pay attention to the warnings that we’ve put in place before they choose to download and install untrusted content."
reader comments
27