No honor among thieves: New ransomware takes your money, deletes files anyway

Ransomware is bad enough, but offers a sliver of hope to victims by promising to give them their files back if they obey instructions -- with the exception of a new strain which has been created for money and nothing else.
Ransomware has become something of a pandemic. The malware family infects systems -- most often through dodgy downloads and phishing campaigns -- in order to encrypt your files. A landing page then informs users that if they give in and pay a ransom in Bitcoin, they will be given the keys back to their kingdom.
The general public, businesses, universities, and even hospitals have been targeted by threat actors utilizing this malicious code, and unfortunately, profits continue to surge as many firms simply give in and pay rather than lose more money due to the disruption.
You are always asked not to pay, as this does nothing more than fuel the problem.
Now, a new ransomware strain will not unlock your files even if you do.
According to the Cisco Talos security team, a new variant of ransomware dubbed "Ranscam" is now targeting users. The ransomware is barely more than a shadow of "true" ransomware such as Cryptowall or TeslaCrypt; as it lacks complexity and any real features when it comes to decryption or file recovery.
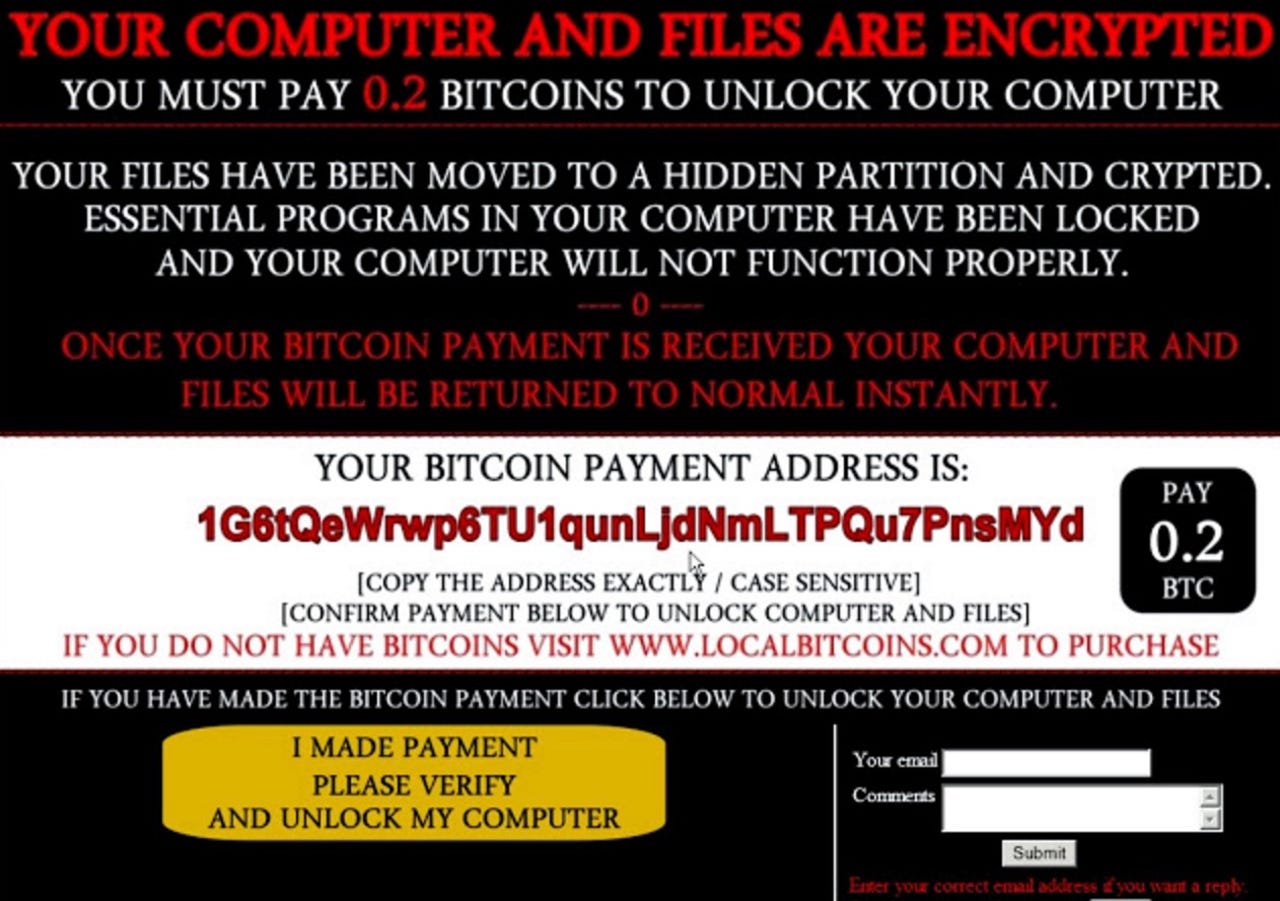
The malware claims to encrypt victim files, throws up a landing page and demands 0.2BTC before piling on the pressure by claiming that for each click made on the compromised system which is not related to payment, files are deleted.
This, however, is a complete lie.
"There is no longer honor amongst thieves," Talos noted. "Ranscam simply delete victims' files, and provides yet another example of why threat actors cannot always be trusted to recover a victim's files, even if the victim complies with the ransomware author's demands."
The ransom note also says that the victim's files have been moved to a "hidden, encrypted partition," which is unusual as most threats simply state that the files in question are still in their original locations, but are encrypted to restrict access.
In addition, the malware displays the note after each reboot following the original compromise -- and the landing page is just a .JPEG file stored on the user's desktop together with two framed elements retrieved through the Internet Explorer browser.
Should a victim pay up, they can choose to click a button which claims to verify payment. In reality, no verification occurs -- as clicking the button does nothing than pull up additional images which state that the verification failed and a fresh file will be deleted for every click until payment is made.
In other words, pressure is used to try and coerce the victim into paying up -- but the reality is that every shred of hope is fruitless. The files have already been deleted and the malware has no functionality which can recover or restore files.
Instead of encrypting files, Ranscam rifles through user directories and simply wipes out data. In addition, the malware destroys core Windows files necessary for system restores, deletes shadow copies and also removes registry keys needed to enter Safe Mode or Task Manager -- making sure that a completely fresh install is the only thing victims can do.
The researchers say:
"The lack of any encryption (and decryption) within this malware suggests this adversary is looking to 'make a quick buck' - it is not sophisticated in any way and lacks functionality which is associated with other ransomware such as Cryptowall."
As the threat actor did not bother to set up different Bitcoin wallet addresses to elicit payment from victims, the team was able to track down the transactions made because of Ranscam infection. In total, only $277.61 has been forwarded to the cyberattacker.
Despite the shoddy malware, if infected, it is the lack of work put into the code which destroys all hope of file restoration.
"This appears to be an amateur malware author and is not a sophisticated campaign," Talos says. "The main component of Ranscam is scaring victims into paying, and they do not even manage to facilitate that at times due to failures in the frame rendering used to deliver their malware payment screen."