
If it wasn't already obvious, pirating software is a risky business and this was again proven by a set of malicious executables targeting macOS users with info stealers and adware, and compiled as Windows EXE binaries with the help of the open source Mono framework.
Mono is designed to allow developers to create cross-platform .NET applications part of the .NET Foundation, which can be later used on multiple platforms, from macOS, Windows, Android, most Linux distributions, BSD, and Solaris, as well as on some game consoles such as PlayStation, Xbox, and Wii.
The malware ridden executables discovered by Trend Micro's Don Ladores and Luis Magisa are distributed via torrent websites and promise to deliver cracked versions of various software:
- Little_Snitch_583_MAC_OS_X.zip
- Paragon_NTFS_for_Mac_OS_Sierra_Fully_Activated.zip
- Wondershare_Filmora_924_Patched_Mac_OSX_X.zip
- LennarDigital_Sylenth1_VSTi_AU_v3_203_MAC_OSX.zip
- Sylenth1_v331_Purple_Skin__Sound_Radix_32Lives_v109.zip
- TORRENTINSTANT.COM+-+Traktor_Pro_2_for_MAC_v321.zip
Mono-based binaries will launch unhindered as long as the Mono runtime is available on the system and the threat actors made sure that their malware will be able to run by bundling a copy of the Mono framework within the downloaded installers.
The installer within the Little_Snitch_583_MAC_OS_X.zip (the one Trend Micro chose to analyze) looks just like any other macOS app, but on closer inspection, when looking within the application bundles, the researchers were able to find the maliciously crafted EXE files which will deliver "a malicious payload that overrides Mac’s built-in protection mechanisms such as Gatekeeper."
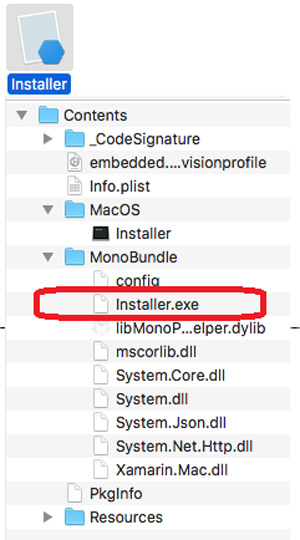
The fact that running Windows executables files is not commonplace on macOS (actually, trying to do so will only display an error), allows the malicious EXE files to circumvent macOS' Gatekeeper protection mechanism which does not recognize them as a native binary, and will not check their notarization status and Developer ID signature.
"While no specific attack pattern is seen, our telemetry showed the highest numbers for infections to be in the United Kingdom, Australia, Armenia, Luxembourg, South Africa and the United States," says Trend Micro.
After being launched on the victim's Mac, the malware will automatically start collecting system information (i.e., ModelName, ModelIdentifier, ProcessorSpeed, ProcessorDetails, NumberofProcessors, NumberofCores, Memory, BootROMVersion, SMCVersion, SerialNumber, UUID.)
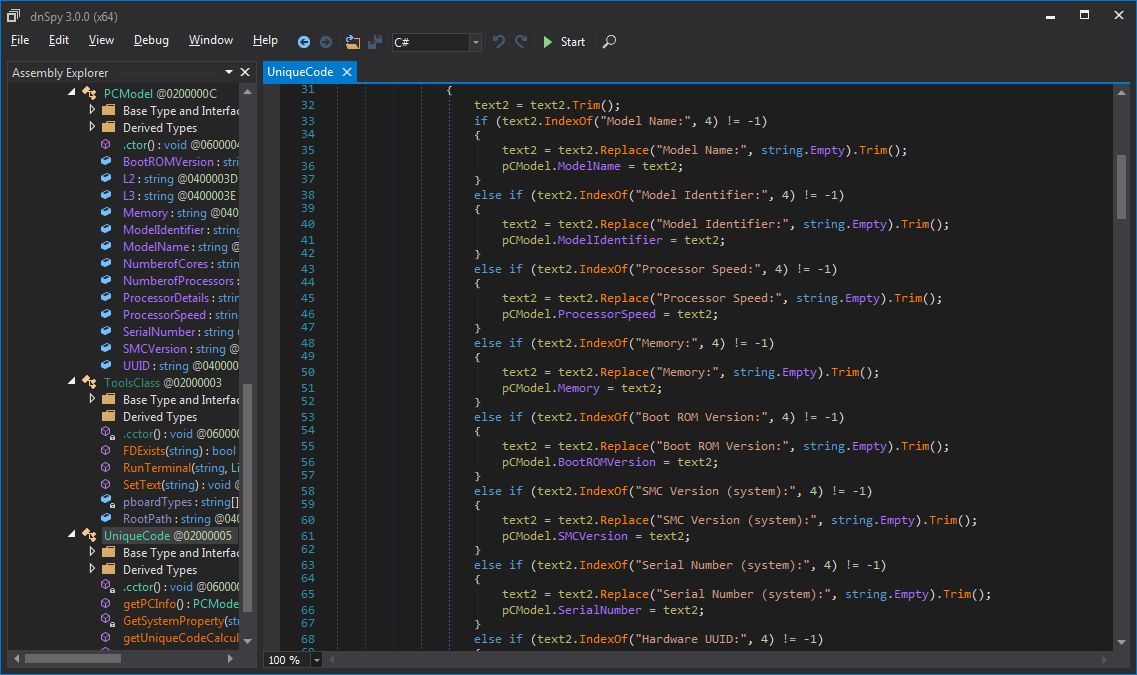
In the next step, it will also list all the apps installed on the Mac and will exfiltrate all the information it has collected to its command-and-control (C&C) server.
While there is no obvious purpose for gathering this info, the bad actors can later use it to generate stats on a potential botnet if they ever decide to build one using the compromised Macs.
Next, it grabs the following files, stores them into ~/Library/X2441139MAC/Temp/, mounts them as DMG images, and executes the binaries contained within:
- hxxp://install.osxappdownload.com/download/mcwnet
- hxxp://reiteration-a.akamaihd.net/INSREZBHAZUIKGLAASDZFAHUYDWNBYTRWMFSOGZQNJYCAP/FlashPlayer.dmg
- hxxp://cdn.macapproduct.com/installer/macsearch.dmg
InstallCapital pushed as payload
From tests conducted by BleepingComputer, the main payload in the malicious executable pushes a pay-per-install adware bundle from monetization company InstallCapital.
InstallCapital is a well-known adware bundle commonly used as part of Windows-based payloads to install numerous unwanted programs including, adware, unwanted extensions, miners, and even drop some ransomware strains at times.
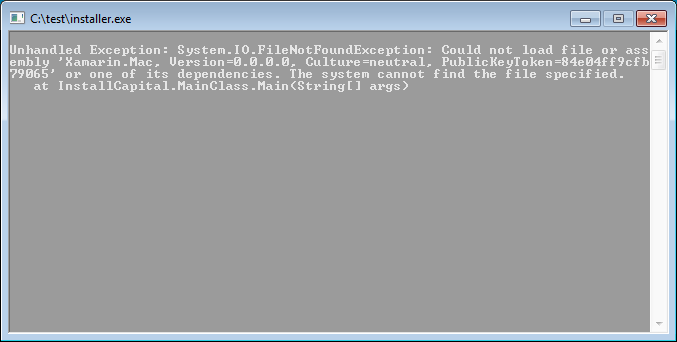
While the malware's developers used an unorthodox approach to deliver Windows-based payload components such as InstallCapital, their malicious EXE binary will not run on Windows systems because it looks specifically for the Mac Xamarin libraries when launched and it will only throw an unhandled exception error before abruptly shutting down.
Trend Micro's research team concludes that "this specific malware can be used as an evasion technique for other attack or infection attempts to bypass some built-in safeguards such as digital certification checks since it is an unsupported binary executable in Mac systems by design."
Although, at the moment, this cross-platform malware only pushes adware and information stealers to Mac users who risk downloading cracked software, in the future the payload can change at any time to drop more dangerous malware families such as ransomware or wipers.
Indicators of compromise such as SHA256 hashes for the executables unearthed by Trend Micro on torrent websites and C&C server addresses are provided at the end of their analysis.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now