macOS Gatekeeper 'easily' fooled into running malicious apps, says researcher
A security researcher has detailed how a user can be tricked into running potentially malicious applications, bypassing Gatekeeper, with the disclosure three months after he's told Apple.
Security consultant Filippo Cavallarin says that a flaw in the design of macOS makes it "possible to easily bypass Gatekeeper," Apple's system that is intended to prevent users from running potentially malicious apps. He reported the flaw to Apple on February 22, 2019, and is now revealing it publicly.
"This issue was supposed to be addressed, according to the vendor, on May 15th, 2019," writes Cavallarin on his website, "but Apple started dropping my emails. Since Apple is aware of my 90 days disclosure deadline, I make this information public."
Ordinarily, if a user downloads an app from somewhere other than the Mac App Store, Gatekeeper will check that it has been code-signed by Apple and is therefore from a legitimate source. If it is not, the application does not launch and the user is told. The user can then force it to launch, but that's a positive choice and takes a little effort, it can't be done accidentally or unknowingly.
According to Cavallarin, however, this can all be circumvented. "As per-design, Gatekeeper considers both external drives and network shares as safe locations," he says, "and it allows any application they contain to run."
The idea is that once you've downloaded it and made your choice about launching the app, Gatekeeper doesn't keep checking it every time you want to open it.
However, you can be tricked or manoeuvred into mounting a network share that isn't yours and the folder in question can contain anything, including zip files with another part of the vulnerability.
"Zip archives can contain symbolic links pointing to an arbitrary location (including automount endpoints)," continues Cavallarin, "and that the software on MacOS that is responsible to decompress zip files do[es] not perform any check on the symlinks before creating them."
Consequently, if the user mounts this network share, unzips a file and clicks the link, they're opening their Macs up to problems. "Now the victim is in a location controlled by the attacker but trusted by Gatekeeper, so any attacker-controlled executable can be run without any warning," concludes Cavallarin. "The way Finder is designed... makes this technique very effective and hard to spot."
Filippo Cavallarin describes himself as a "cybersecurity expert and software engineer," and works for Segment Srl, in Venice, Italy. He has spoken at TEDx Treviso about security issues.
Apple has not commented.
 William Gallagher
William Gallagher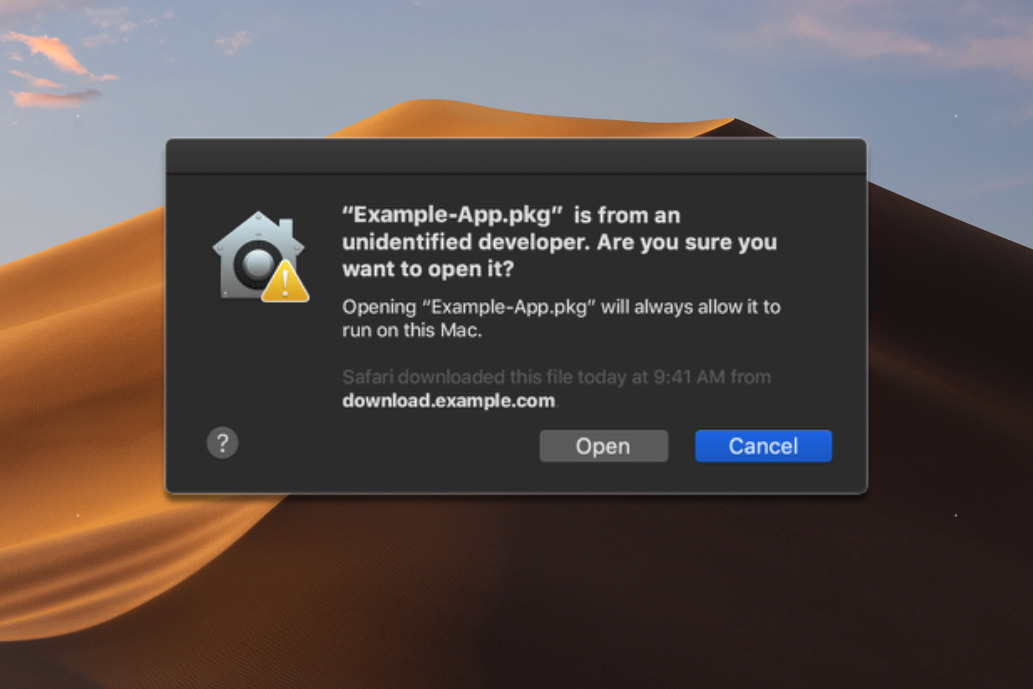











 Andrew Orr
Andrew Orr
 Malcolm Owen
Malcolm Owen



 Mike Wuerthele
Mike Wuerthele
 Christine McKee
Christine McKee